On this Page
| Table of Contents | ||||
|---|---|---|---|---|
|
Snap type: | Transform | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Description: | Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is popularly used to digitally sign, encrypt or decrypt email messages or files being transferred over the Internet.
This Snap encrypts the data provided as an input stream using a public key. This Snap should be attached to the input binary data stream to be encrypted in the pipeline.
| |||||||||||||
| Prerequisites: | [None] | |||||||||||||
| Support and limitations: | Works in Ultra Task Pipelines. | |||||||||||||
| Account: | This Snap uses account references created on the Accounts page of SnapLogic Manager called the PGP Public Key Account that stores the public key used for encryption. See Configuring Binary Accounts for information on setting up this type of account. When setting up the account, enter your public PGP key. The credentials setup will automatically encrypt the message. For signed encryption, this Snap uses account references created on the Accounts page of SnapLogic Manager called the PGP Private Key Account that stores the public and private key used for signed encryption. See Configuring Binary Accounts for information on setting up this type of account. When setting up the PGP Private Key account, enter your public and private PGP keys. The credentials setup will automatically encrypt and sign the message. | |||||||||||||
| Views: |
| |||||||||||||
Settings | ||||||||||||||
Label
| Required. The name for the Snap. You can modify this to be more specific, especially if you have more than one of the same Snap in your pipeline. | |||||||||||||
| Symmetric Key Algorithm | Select or enter the symmetric key algorithm that you want to use to encrypt the input file.
The algorithms available for this field are as follows:
Example: AES_256 Default value: CAST5 | |||||||||||||
Encrypted Filename | Required. For most use cases, this property may be left empty. A temporary file is used during the encryption and deleted by the Snap when it is done. If this property is empty, the Snap automatically generates a temporary filename.
Example: sample.tmp Default value: [none] | |||||||||||||
| Sign in | Sign encrypted file. Enabling this check box requires a Private Key Account. Default value: Not selected | |||||||||||||
|
| |||||||||||||
Examples
The following example includes: Sample input data which is successfully encrypted using the PGP Encrypt Snap and then decrypted using the PGP Decrypt Snap.
Encrypting Data Using the PGP Encrypt Snap
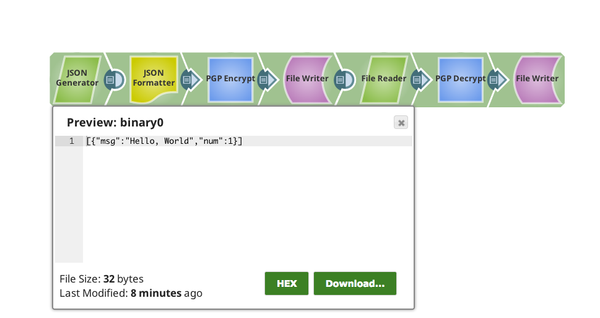
We will start with a JSON Generator Snap which has a sample message "Hello World", which is formatted and written as JSON binary data for the PGP Encrypt Snap to ingest.
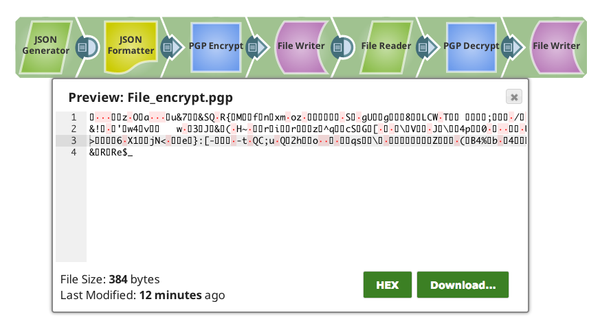
We can see that the Message is Encrypted as the output of the PGP Encrypt Snap.
Decrypted Data Using the PGP Decrypt Snap
We will write the file out as File_encrypt.pgp to the SnapLogic DB. Then we proceed to decrypt the encrypted file and write it to the SnapLogic DB as File_decrypt.txt.
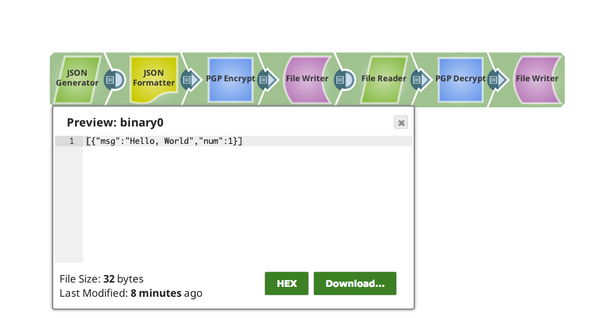
We can see that the output from the Decrypt Snap matches our original raw unencrypted data:
We have successfully decrypted the message.
Downloads
| Info |
|---|
Important Steps to Successfully Reuse Pipelines
|
Attachments
| Attachments | ||||||
|---|---|---|---|---|---|---|
|
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|