In this article
| Table of Contents | ||||
|---|---|---|---|---|
|
Prerequisites
- Familiarity with the SnapLogic and AWS platforms.
- AWS Account with S3 buckets.
Key Steps
Creating a Cross Account IAM Role with trust entity pointing to external account.
- Creating a Storage Integration in Snowflake and generating Account ID and External ID.
- Associating the IAM Policy to the Created Role
Creating a Cross Account IAM Role and Policy in AWS Account
Cross Account IAM Role enables a client from an AWS account to access the resources of another AWS account temporarily using the Binary Snaps that support reading from/writing into S3 buckets. This helps organizations or different teams in an organization to access each other's AWS account without compromising security by sharing AWS credentials.
You can briefly allow access to your AWS account and specify the access duration. You must create a role and policy in your AWS account. The policy created by the host is attached to the access seeker's account. This cross account IAM role enables SnapLogic to trigger the necessary APIs.
Steps
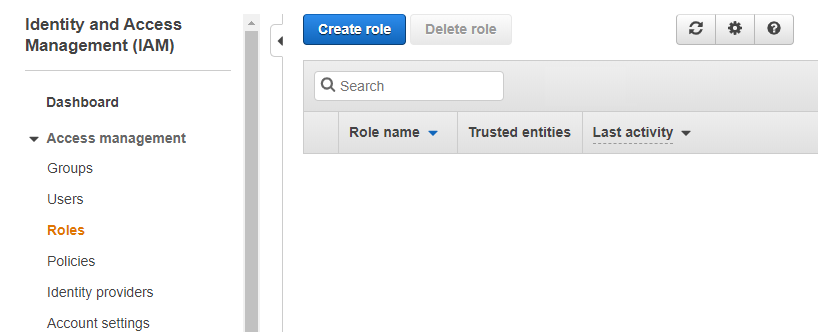
- Log in to the AWS Management Console and go to IAM > Roles.
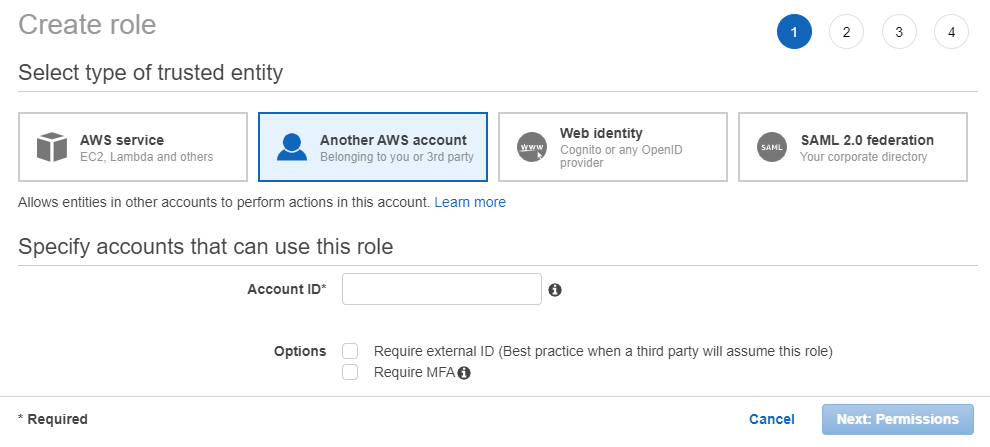
- Click Create role > Another AWS Account. This is where you specify the account ID for the other account, that will access your account.
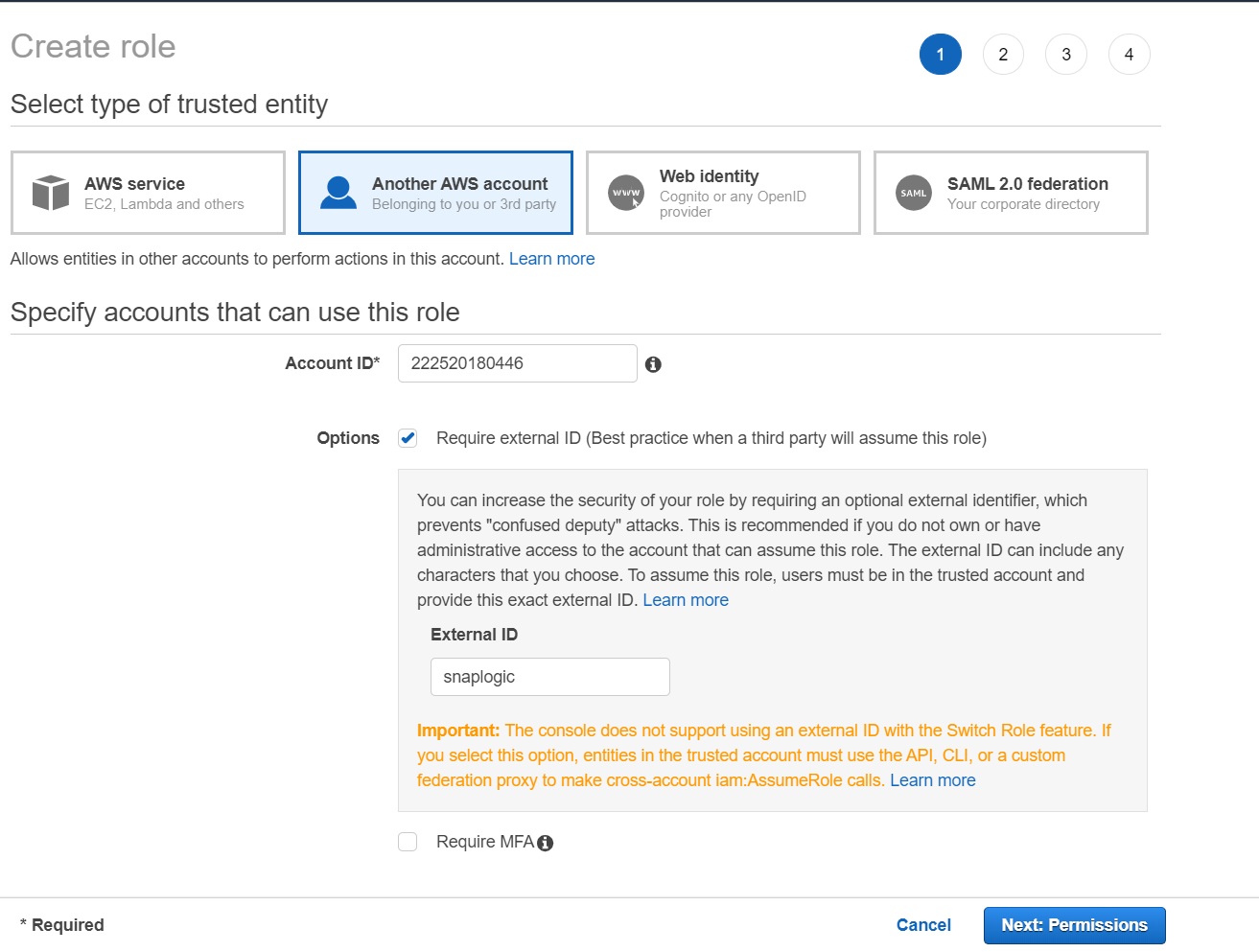
- Enter the account number of the access seeker in the Account ID field, which is available in the Support Center. Optional. Add an additional security layer to authenticate for each login by checking Options check box, next to Require external ID... this role).
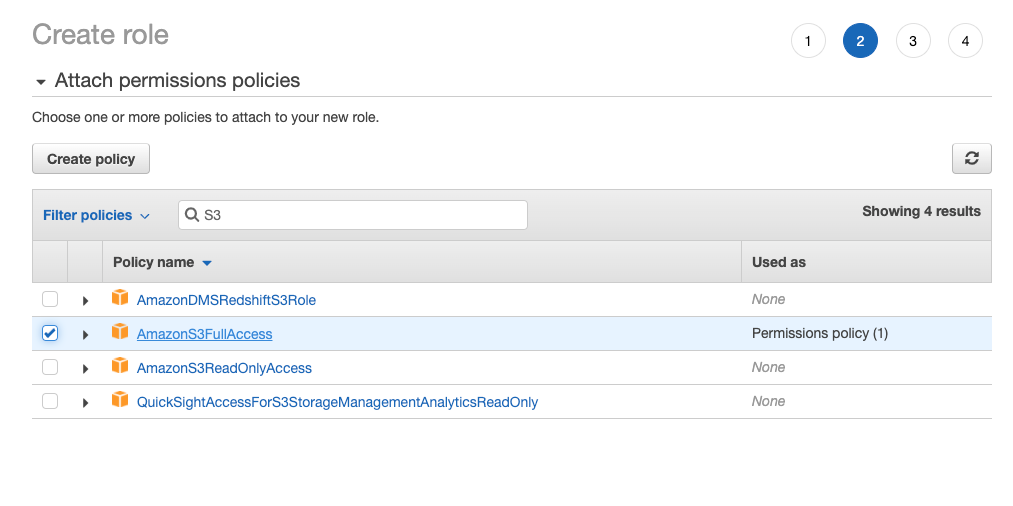
- Click Next: Permissions. The Attach permission policies screen displays, where you can set the permissions. Select the check box next to the applicable policy for this role.
- Click Next: Tags. Optional. Add tags as appropriate. This is an optional step.
- Click Next: Review to skip to the next screen.
- Review the information displayed and add a name for the role. Click Create role.
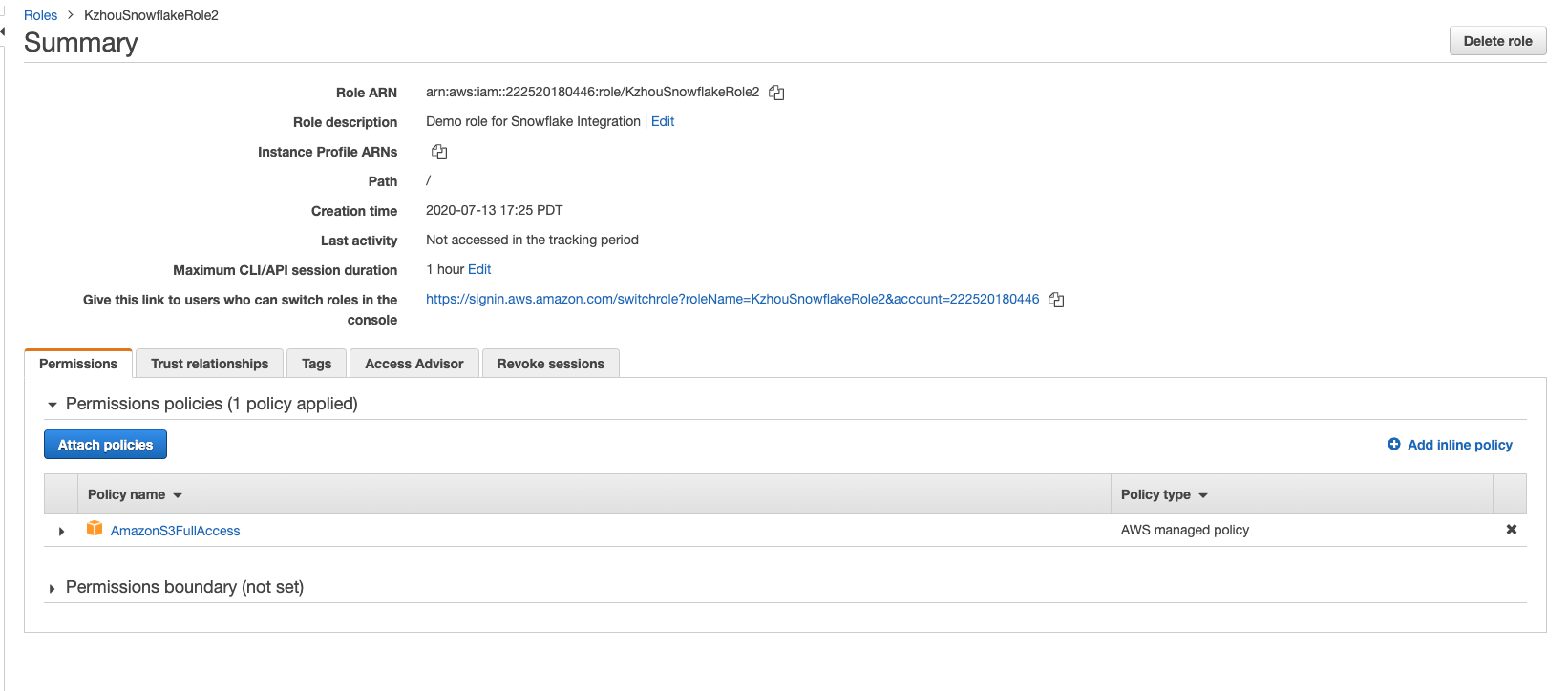
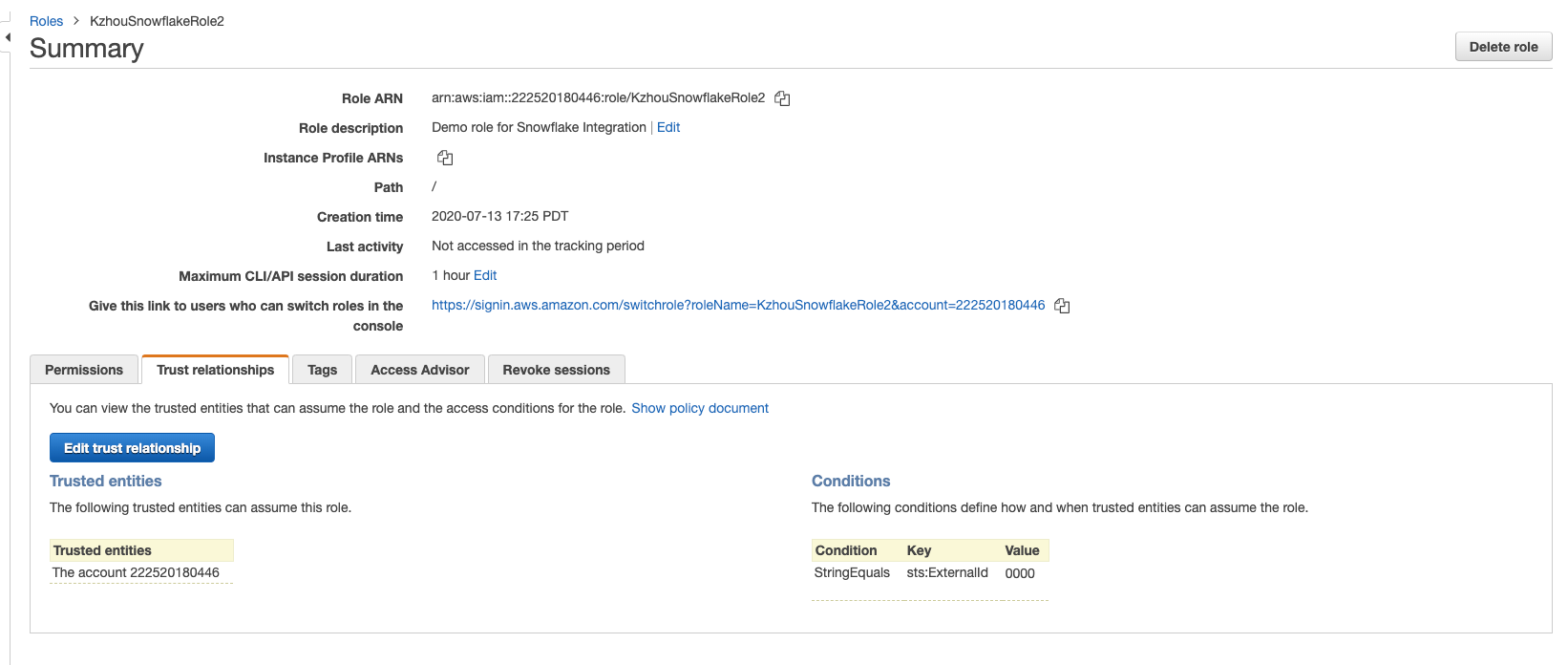
The Summary page displays the Amazon Resource Name number. Make a note of this ARN, as you will need it when completing the AWS IAM Role account settings.
Create Storage Integration or External Stage
In this step, you will create the Snowflake’s account ID and external ID on the Snowflake side to establish the trust entity. You can either create a Storage Integration or an External Stage depending on your need.
Storage Integration
| Note |
|---|
You would require a ACCOUNTADMIN role to create a Storage Integration in Snowflake. |
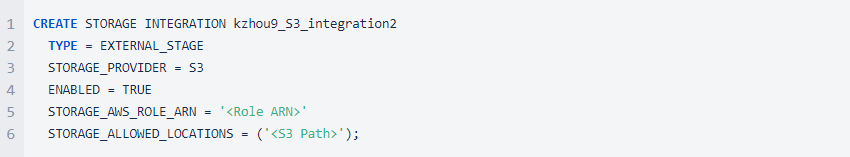
- Create the Storage Integration with the following SQL query:
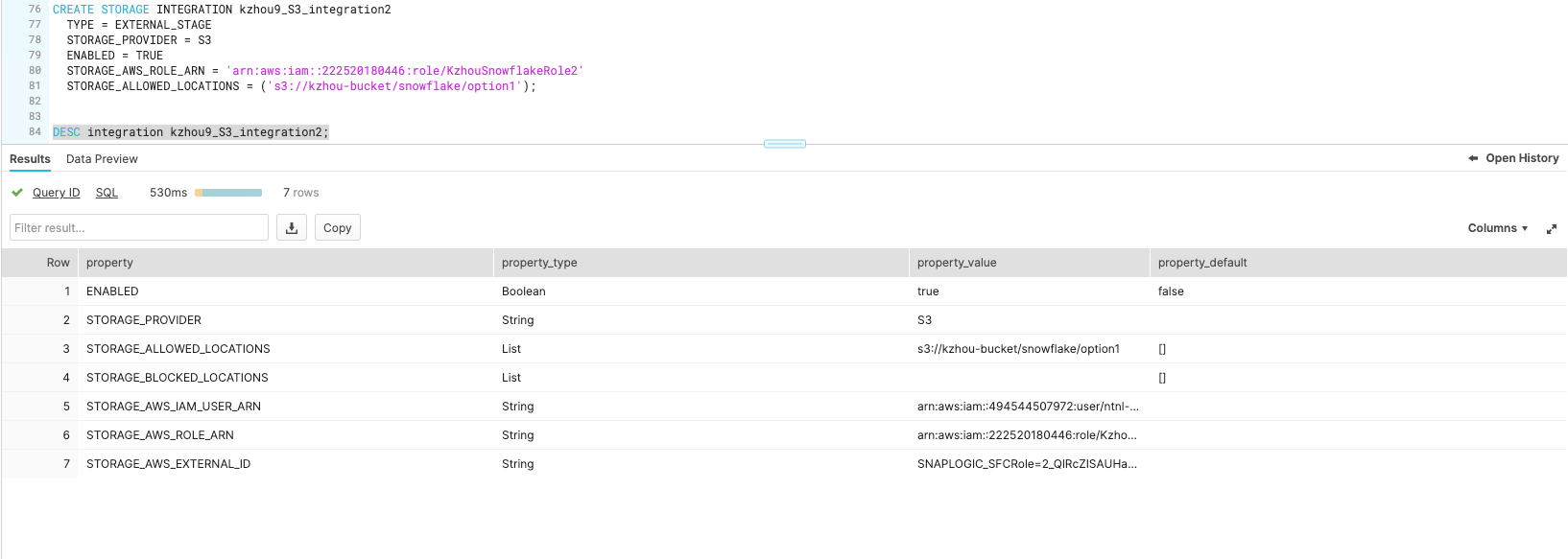
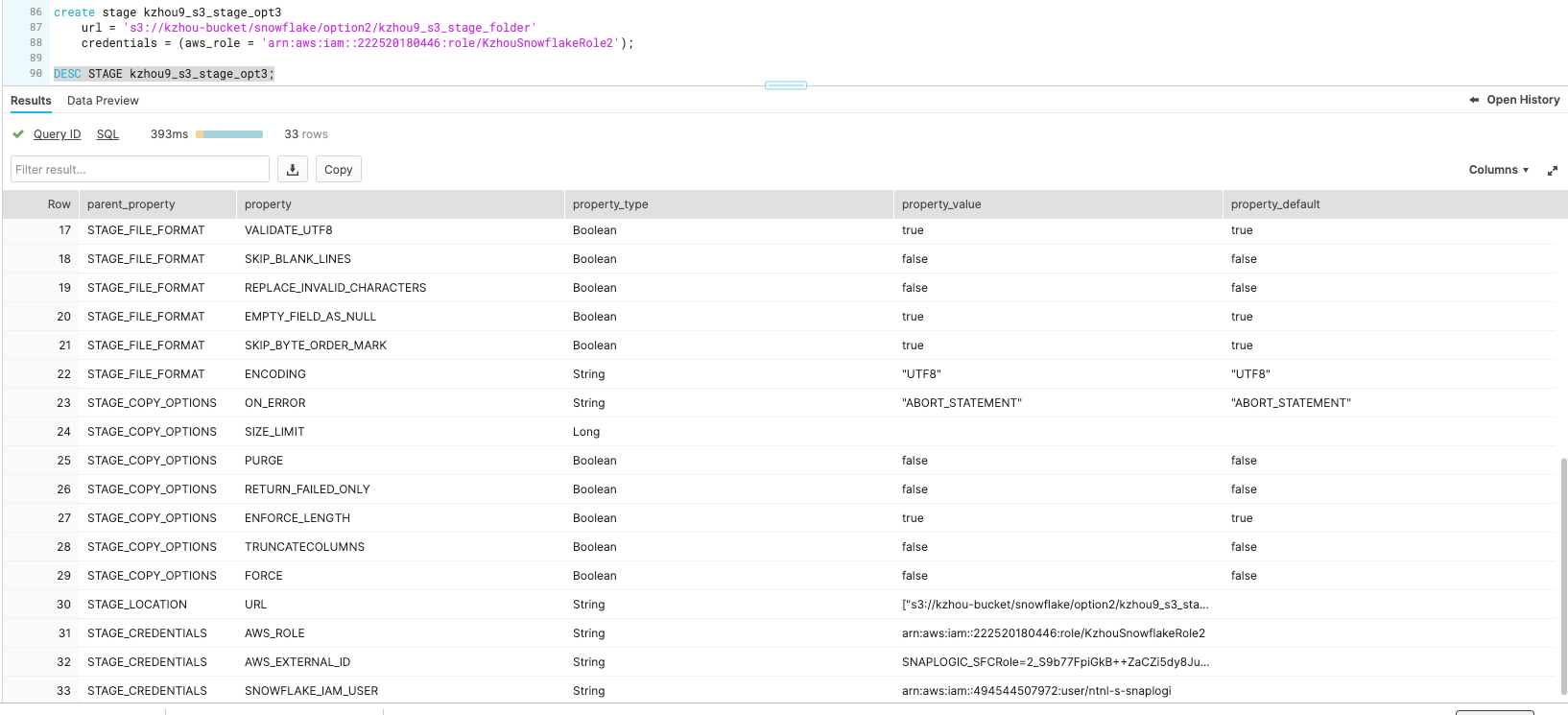
2. Replace the <Role ARN> and <S3 Path> with the corresponding value and list out the details of the created Storage Integration using 'DESC'.
Copy the value of STORAGE_AWS_IAM_USER_ARN as the Snowflake Account ARN, and copy the STORAGE_AWS_EXTERNAL_ID as the external ID.
External Stage
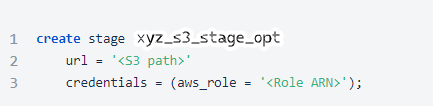
- Create a external named stage through the SQL query.
2. Replace the <Role ARN> and <S3 Path> with the corresponding value and list out the details of the created External Storage using 'DESC'.
Copy the value of SNOWFLAKE_IAM_USER as the Snowflake Account ARN and AWS_EXTERNAL_ID as the External ID.
Associating the IAM Policy with the Created Role
Steps:
- In the Summary screen, under Trust Entity tab and click Edit trust relationship.
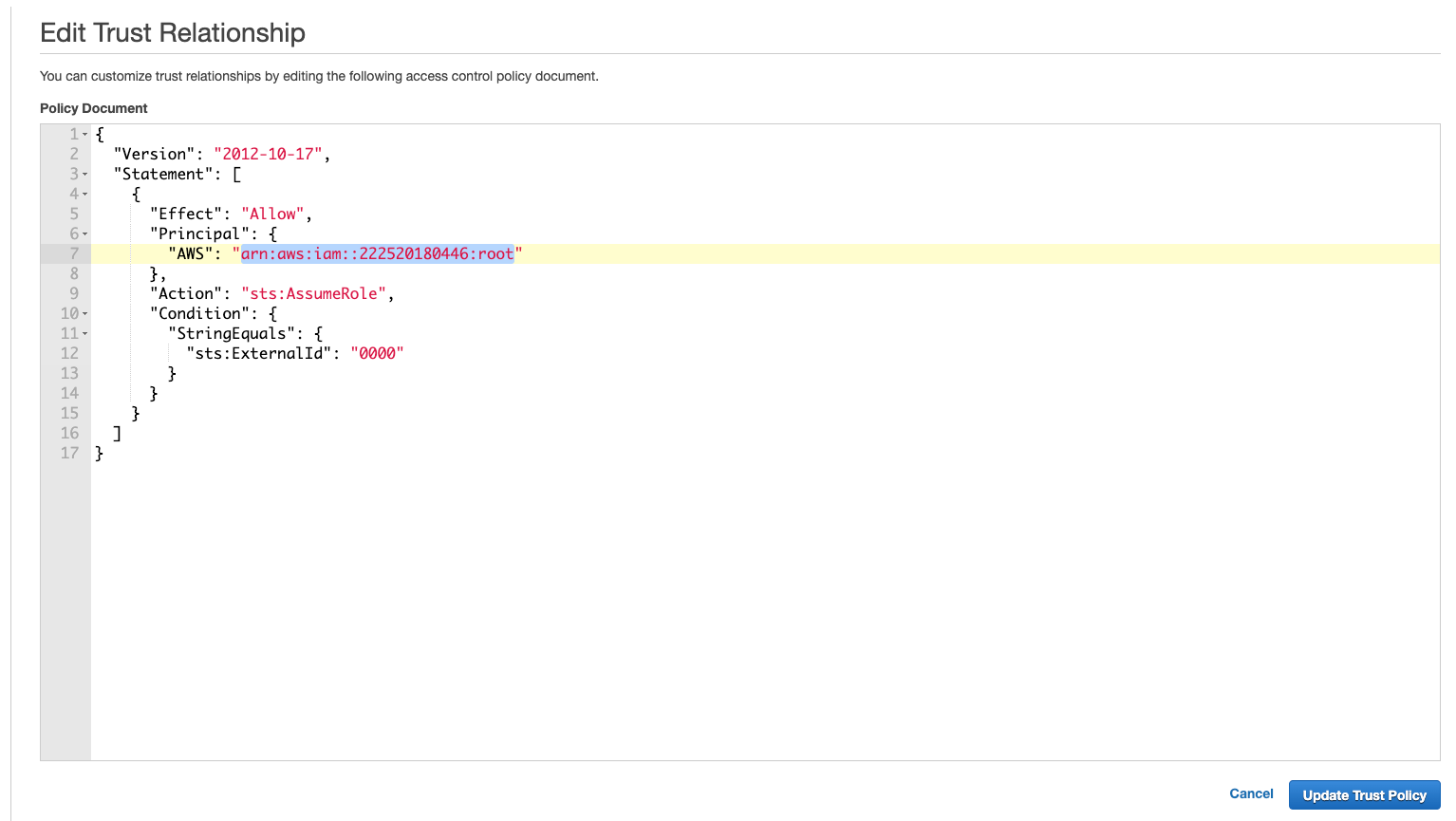
In the editor, replace the value of ‘AWS' with the ARN of the Snowflake Account, and the '
sts:ExternalID’ with the external ID we got from the last step.
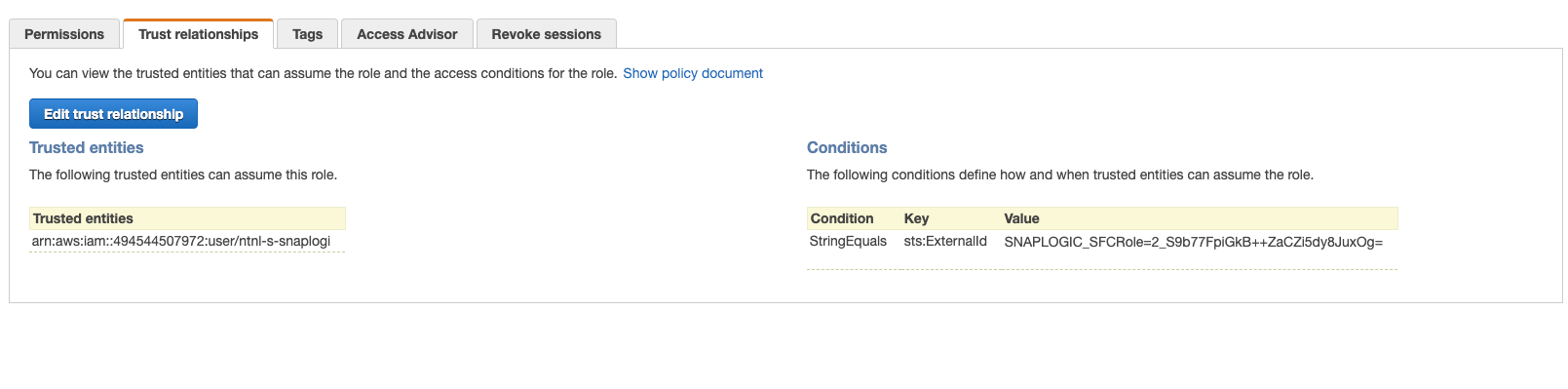
After updating, we will see the trust entity changed accordingly.
The policy is created and can be assigned to the cross-account IAM role.
Account Settings for Access Through SnapLogic
You can configure the cross account IAM Role inside through the Snowflake S3 Database Account or Snowflake S3 Dynamics AccountDynamic Account settings. Enter the credentials provided of related to the IAM role. Enter Role ARN and External ID (if setup by the host) provided from the host S3 account.
Steps
Change the Staging Location to External, which will addGive inputs to S3 Bucket, S3 Folder, S3 Access-key ID, and S3 Secret Key fields respectively.
Steps
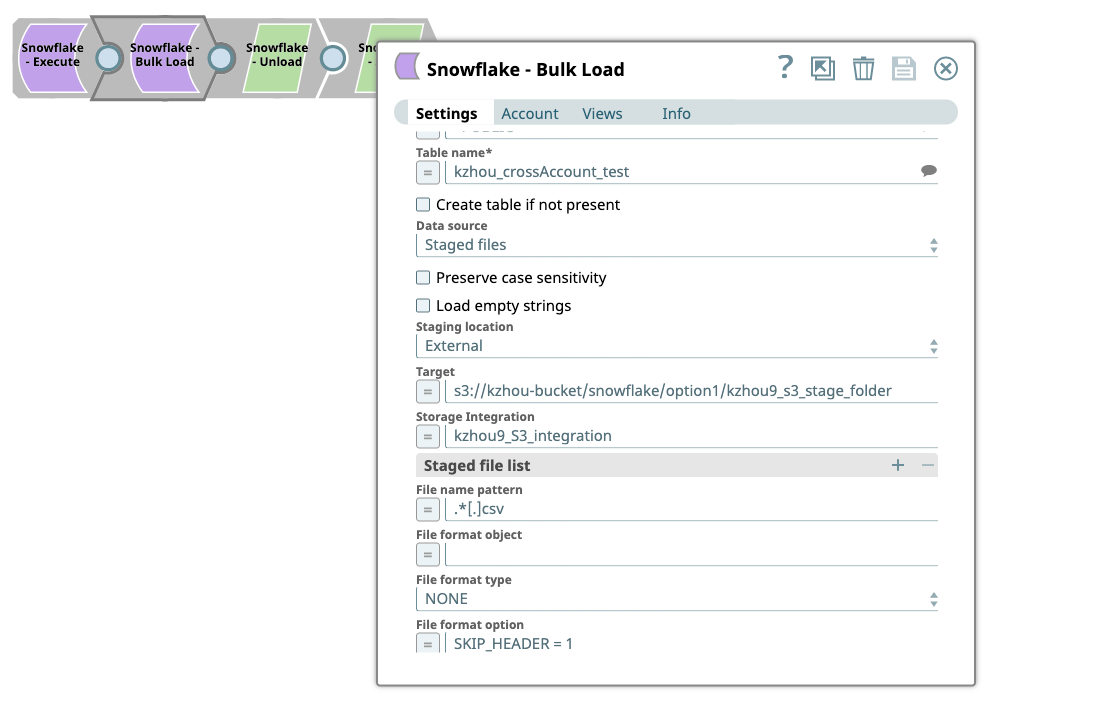
- Select Staged files under Data Source field.
- Select External under Staging Location field, which will enable an extra field, Storage Integration, to the existing Setting fields.
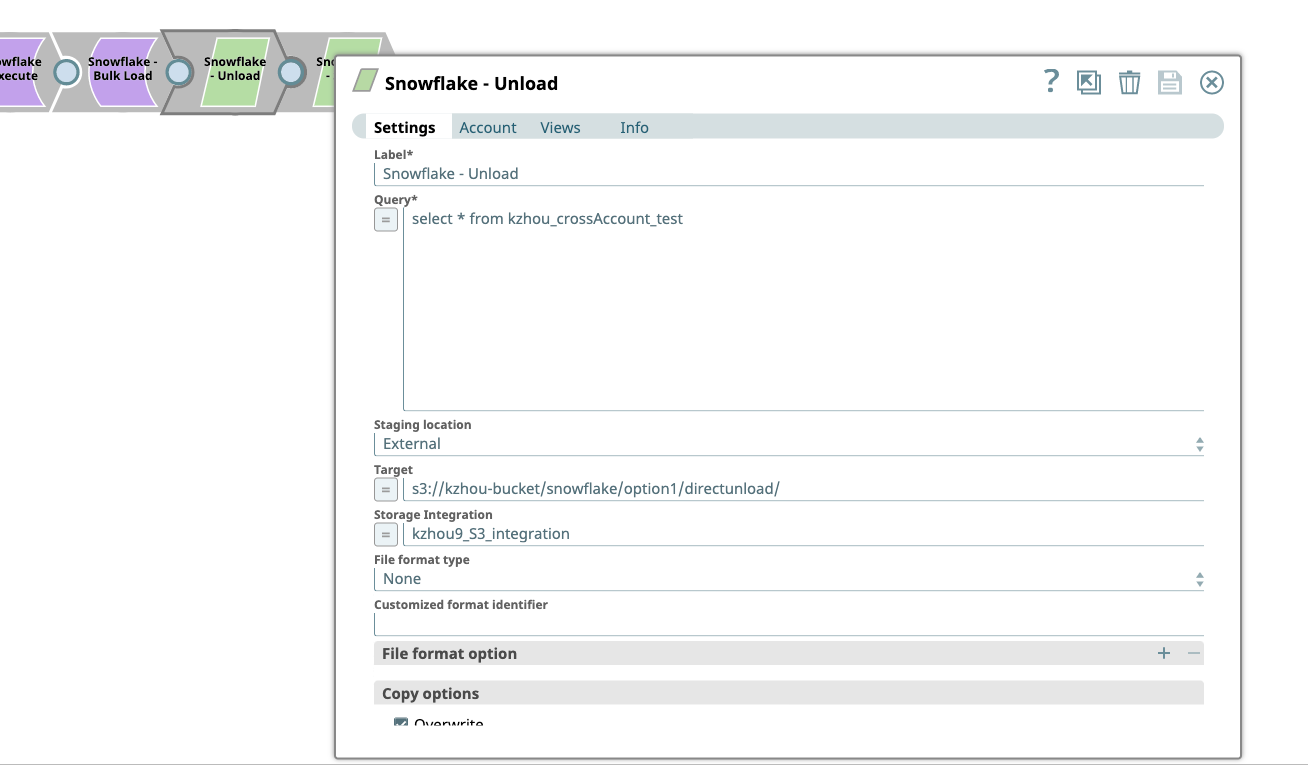
- Select External under Staging Location field, which will enable an extra field, Storage Integration Integration, to the existing Setting fields of the Snowflake Unload Snap.
| Note |
|---|
Once these settings are implied, the Snap would use the Integration as credential to do an unload or bulk load, and ignore the storage credentials in the Account. |