On this Page
| Table of Contents | ||||
|---|---|---|---|---|
|
You can create an account from Designer or Manager. In Designer, when working on pipelines, every Snap that needs an account prompts you to create a new account or use an existing account. The accounts can be created in or used from:
- Your private project folder: This folder contains the pipelines that will use the account.
- Your Project Space’s shared folder: This folder is accessible to all the users that belong to the Project Space.
- The global shared folder: This folder is accessible to all the users within an organization in the SnapLogic instance.
Prerequisites
The s3:ListAllMyBuckets permission is required to successfully validate an S3 account. Refer to the Account Permissions section below for additional permissions required for the target resources based on the task to be performed.
Account Configuration
In Manager, you can navigate to the required folder and create an account in it (see Accounts). To create an account for binary files:
- Click Create, then select Binary, then S3 Dynamic.
- Supply an account label.
Supply the necessary information.
- (Optional) Supply additional information on this account in the Notes field of the Info tab.
- Click Apply.
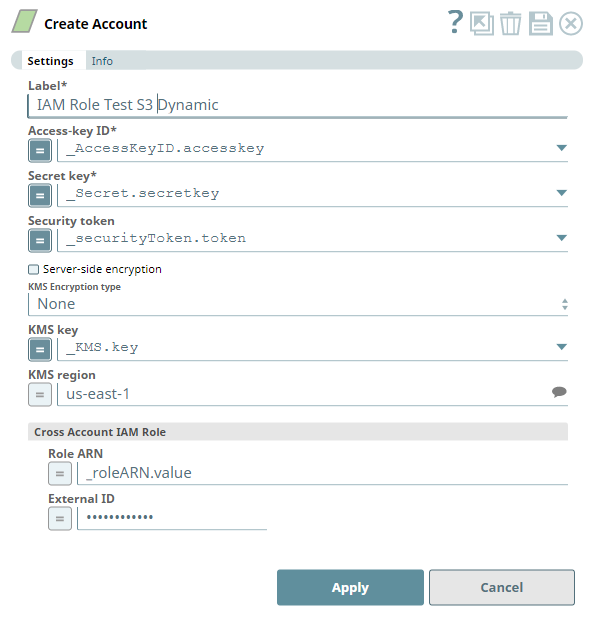
Account Settings
Label | Required. User provided label for the account instance | |||
|---|---|---|---|---|
Access-key ID | Required. Access key ID part of AWS authentication Default value: [None] | |||
Secret key | Required. Secret key part of AWS authentication Default value: [None] | |||
| Security Token | Required. Security token part of AWS Security Token Service (STS) credentials | |||
| Server-side encryption | This represents the type of encryption to use for the objects stored in S3. For Snaps that write objects to S3, this field defines how the objects will be encrypted. For Snaps that read objects from S3, this field is not required. Default value: Not Selected | |||
| KMS Encryption type | This field represents the AWS Key Management Service key used to encrypt S3 objects. It can be the key ID or ARN. For Snaps that write objects to S3, this is required for encryption types Server-Side encryption with AWS KMS-Managed Keys and Client-Side encryption with AWS KMS-Managed Keys. For Server-Side encryption, the key must be in the same region as the S3 bucket. For Client-Side encryption, a key from any region can be used by using the key ARN value. If a key ID is used for Client-Side encryption, it defaults to the us-east-1 region. For Snaps that read objects from S3, this field is not required. The available options are:
Default value: None | |||
| KMS key | This field represents the AWS Key Management Service key used to encrypt S3 objects. It can be the key ID or ARN. For Snaps that write objects to S3, this is required for encryption types Server-Side encryption with AWS KMS-Managed Keys and Client-Side encryption with AWS KMS-Managed Keys. For Server-Side encryption, the key must be in the same region as the S3 bucket. For Client-Side encryption, a key from any region can be used by using the key ARN value. If a key ID is used for Client-Side encryption, it defaults to the us-east-1 region. For Snaps that read objects from S3, this field is not required. Default value: [None] | |||
| Cross Account IAM Role | This field set helps in granting cross account access, with two fields:
| |||
| Role ARN | The Amazon Resource Name of the role to assume. Default value: [None] | |||
| External ID | An optional external ID that might be required by the role to assume. Default value: [None] | |||
Account Encryption
| Standard Encryption | If you are using Standard Encryption, the High sensitivity settings under Enhanced Encryption are followed. | |
|---|---|---|
| Enhanced Encryption | If you have the Enhanced Account Encryption feature, the following describes which fields are encrypted for each sensitivity level selected per each account. Account:
| |
| Multiexcerpt include macro | ||||
|---|---|---|---|---|
|