...
- OpenAM
- Microsoft Azure Active Directory (AD)
- OKTA
- Ping
Additional methods may work, but have not been verified by SnapLogic.
SAML Overview
The SAML standard defines how Service Providers (SP) can communicate with Identity Providers (IdP) to securely authenticate users. In this case, SnapLogic is the Service Provider and OpenAM is the Identity Provider. The communication between the two starts after the user enters their organization name and clicks the SSO Log In button on the SnapLogic home page. The SnapLogic server uses the organization name to find the associated IdP and then redirect redirects the user's web browser to that IdP with an authentication request. The destination for the redirect is defined by the IdP metadata file that is uploaded when configuring the user's organization to use SSO.
After the IdP receives the authentication request, it validates the request to ensure it is coming from a known Service Provider (SP) and then redirects the users user's browser back to SnapLogic. The IdP is informed of the SnapLogic service by uploading the SnapLogic metadata file that is generated when configuring the user's organization to use SSO. Finally, the authentication response is validated by the SnapLogic server using the IdP metadata and the user is allowed to begin working in the SnapLogic Designer.
...
| Note | ||
|---|---|---|
| ||
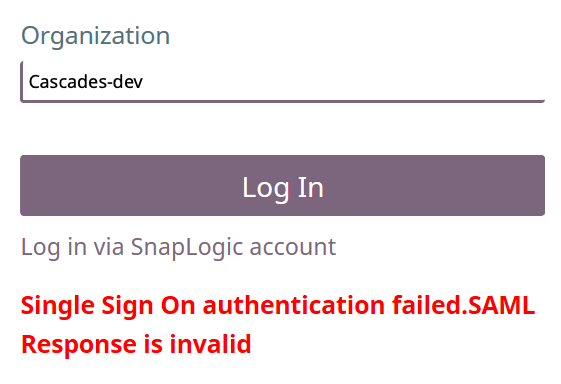
Some SSO implementations use an IdP metadata file for multiple Orgs. We support allowing users access to only their Org in this implementation of SSO. Users who belong only to one Org (and not the other Orgs) can now log into SnapLogic regardless of which Org the IdP metadata references. For example, previously in this scenario, If you belonged to OrgB, but the IdP used OrgA's metadata, then your login to OrgB would fail with the following error message: |
Manage SSO Options
You can customize the the SSO login with additional authentication at the Org level using the Manage SSO Options feature. This feature enables you to configure AuthnRequest, RequestedAuthN Context Comparison, and AuthNContextClassRef authentication methods after uploading the IdP metadata file.
...
Users can be granted access to multiple organizations in the SnapLogic Integration Platform. Logging into the SnapLogic platform through SSO does not affect which organizations the user has access to. For example, if "Alice" is a member of "Company 1" and "Company 2" and she logs in via the IdP for "Company 1", she is still be able to access "Company 2". The authentication process only validates that the person logging into the service is who she say says she is; it does not control what she has access to. However, there cannot be multiple different IdPs configured on those Orgs.
...
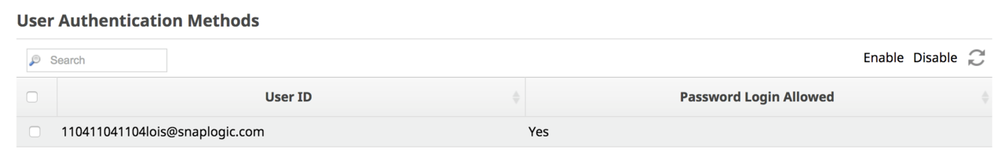
To set accounts to use or not use the SnapLogic login mechanism, click the Manage Password Logins button on the Settings page in Manager to get to the User Authentication Methods page. Then select the users necessary and click Enable or Disable as needed.
...
Related Content
- Two-way SSL with SnapLogic’s REST Snap
- Configuring Azure Active Directory SSO Configuration with SnapLogic
...