In this article
| Table of Contents | ||
|---|---|---|
|
Overview
All SnapLogic endpoints use the Standard Encryption setting by default. As an Org admin using Groundplex instances to run your Pipelines, you can encrypt Account credentials that access endpoints from SnapLogic using data/server keys.
| Warning | ||
|---|---|---|
| ||
We strongly recommend that you make backup copies of your data keys. Otherwise, if the data keys to your account become corrupted or are unrecoverable, then all sensitive fields in the accounts would have to be manually re-entered to recover the accounts. |
| Note | ||
|---|---|---|
| ||
|
Enabling Enhanced Account Encryption
Prerequisites
- Google Chrome version 37 and later.
- A Groundplex. Windows and Linux machines are supported, but if you plan to host your Snaplex instances in an mixed ecosystem (Windows and Linux OS), the server and data keys must be encrypted on a Linux machine to be used on a Linux-based Snaplex.
- If you are using Linux, make sure you have the latest install of the RPM/DEB on each Groundplex node.
- A Java 11 environment.
Preparing Groundplex Nodes for Enhanced Encryption
SnapLogic Enhanced Encryption makes use of key sizes that are not supported in the standard installation. After restarting the service, a new key pair is generated automatically and saved to disk, per JCC node. You must copy the generated data keys files (jcc-datakeys.jks and jcc-datakeys.pass) from one node to all of the others in the Groundplex.
| Note | ||
|---|---|---|
| ||
Server keys ( |
Using a Linux machine
...
Using a Windows machine
| Note | ||
|---|---|---|
| ||
Data keys are the same across JCC nodes; however, the server keys are unique for each JCC node. You should generate the data keys on a Linux machine and copy them to the SL_KEY_DIR folder on the Windows machine. Only the security administrators and users that run the Groundplex service must have access to the directory. |
...
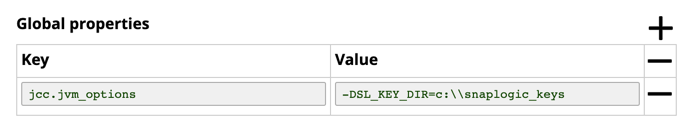
Click the Node Properties tab, and under Global Properties, click to enter the key-value pair.
...
Add the following in the Snaplex property:
| Paste code macro | ||
|---|---|---|
| ||
jcc.jvm_options = -DSL_KEY_DIR=c:\\snaplogic_keys |
...
Applying Enhanced Account Encryption to your Org
To configure Enhanced Account Encryption on a Groundplex for your SnapLogic Org:
...
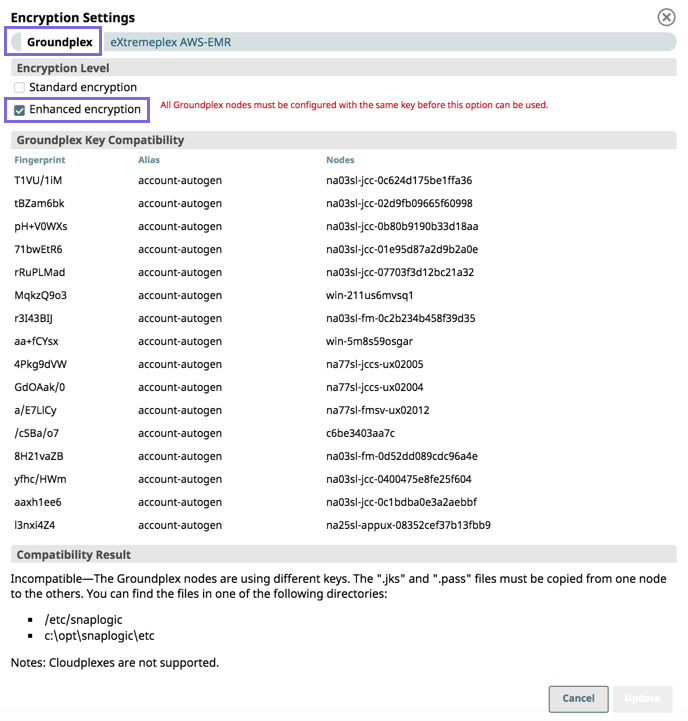
On the Encryption Settings dialog, click the Groundplex tab (default), then select Enhanced encryption.
...
Verify that the same key is used on all nodes of the Groundplex; otherwise, you cannot configure the Org with Enhanced Encryption because all keys used across an Org must be consistent
Select the level of sensitivity based on the following:
...
Low, Medium, and High. Encrypts host name, database names, database URL properties, usernames, passwords, and secret keys.
| Info | ||
|---|---|---|
| ||
To learn about which fields are encrypted for an Account, see the sensitivity level definition in the Account’s documentation for that Snap Pack. |
...
To set a key for the entire Org, select the target key. Only those keys that are available on all nodes are displayed.
...
When you view the Org Settings, the new Status displays under Configure Encryption:
Scope and Limitations
- Once Enhanced Account Encryption is enabled, you are not able to see or edit the existing values for the encrypted data types.
However, you are able to enter a new value in that field and save it.
- If you change your sensitivity level from Low, Medium, High to High, existing accounts remain at the previous level unless you update them; going in the other direction causes account data to be encrypted. All new accounts follow the new sensitivity encryption level.
- If you revert to standard encryption, the encrypted data is not automatically decrypted. As long as the server key is still in the node, the encrypted values continue to work.
Key Rotation
To change the enhanced encryption key (key rotation) for an organization, perform the following steps:
...
As root user, run the following command:
| Code Block |
|---|
/opt/snaplogic/bin/jcc.sh addDataKey keyFeb2020 |
...
After you enable Enhanced Encryption on your Groundplex nodes:
- Currently running Pipelines continue when the key is being rotated.
Accounts in the organization are sent to the Groundplex to be decrypted with the old key and then encrypted with the new key.
- Accounts that were exported when the Org ran with the old key have the Sensitivity fields encrypted with the old key. When the account information is imported into the Org after the key is rotated, the account is imported with the old key. To convert these imported accounts to the new key, go to Manager and redo the key rotation with the new key.
- The updates to the key store using the script are supported only on a Linux-based Groundplex machine. The updated key store can be copied to the Windows-based Groundplex machine to ensure that the rotated key is applied on the Windows machine as well. If using a Groundplex on Windows only, you can install the Linux RPM on a stand-alone machine for the purpose of updating the key store using the
jcc.shscript.
Adding Groundplex Nodes
When adding new nodes to a Groundplex, you must ensure that the new nodes have the same key as the other nodes. If a node does not have a matching key, it is ignored until the keys are synchronized. You can redo the configuration through the Enhanced Encryption Settings dialog in the Manager > Settings > Configure Encryption by checking the current key compatibility status.
Updating Windows Groundplex Instances to Use an Encrypted Keystore
To enable Enhanced Encryption on Windows Groundplex instances, the recommended procedure is to generate the keys on a Linux machine and then copy them onto the Windows node. The advantage is that the generated keystore is encrypted, and the same keystore can be used on both Windows and Linux nodes.
If there are existing Windows installations with Enhanced Encryption where the key was not initially generated in Linux, adding new Linux-based nodes require these additional steps, because, in such cases, there would be a datakeys.jks file under the etc folder, with no .pass file.
...
Perform the following steps as the root user.
| Paste code macro | ||||
|---|---|---|---|---|
| ||||
# Perform below operations as root user
# Copy the datakeys.jks file from windows to the Linux machine, file should be placed at /etc/snaplogic/jcc-datakeys.jks
cd /opt/snaplogic
# Generate password file with a secure password. Change RANDOM_SECURE_PASSWORD to a secure password to use for the keystore
export MYPASS=RANDOM_SECURE_PASSWORD
echo -n $MYPASS > /etc/snaplogic/jcc-datakeys.pass
# Encrypt the keystore with the new password
/opt/snaplogic/pkgs/jdk-11.0.8+10-jre/bin/keytool -storepasswd -new $MYPASS -keystore /etc/snaplogic/jcc-datakeys.jks -storepass ""
# Encrypt the key with the same password
/opt/snaplogic/pkgs/jdk-11.0.8+10-jre/bin/keytool -keypasswd -alias account-autogen -new $MYPASS -keystore /etc/snaplogic/jcc-datakeys.jks -storepass $MYPASS -keypass ""
|
| Info |
|---|
You might have to change the JRE version based on the environment first if you are not using Java 11. |
The keystore is now in a format suitable for use on Linux machines. You can now copy the same jcc-datakeys.jks and jcc-datakeys.pass files to other Linux-based nodes without having to repeat the prior steps.
...