On this Page
| Table of Contents | ||||
|---|---|---|---|---|
|
| Snap type: | Read | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Description: | This Snap generates JSON Web Tokens (JWT). Together with the JWT Validate Snap, this Snap allows pipelines the ability to issue and use limited scope access tokens. JSON Web Token (JWT) is an open standard that defines a compact and self-contained way for securely transmitting information (claims) between parties. This information is stored in the token as a JSON object, and is signed using a secret (with HMAC algorithm) or private key (with RSA Algorithm). All the information necessary to validate the token and its contents is contained within the JWT, thereby avoiding an expensive resource look up (for example, a database look up) during token validation. The Snap properties allow users to customize what information gets embedded in the token. Input & Output
| ||||||||||||
| Prerequisites: | [None] | ||||||||||||
| Limitations and Known Issues: |
| ||||||||||||
| Configurations: | Account & AccessThis Snap uses account references created in SnapLogic Manager to handle access to this endpoint. See this article for information on setting up this type of account. Views
| ||||||||||||
| Troubleshooting: | [None] | ||||||||||||
Settings | |||||||||||||
Label | Required. The name for the Snap. You can modify this to be more specific, especially if you have more than one of the same Snap in your pipeline. | ||||||||||||
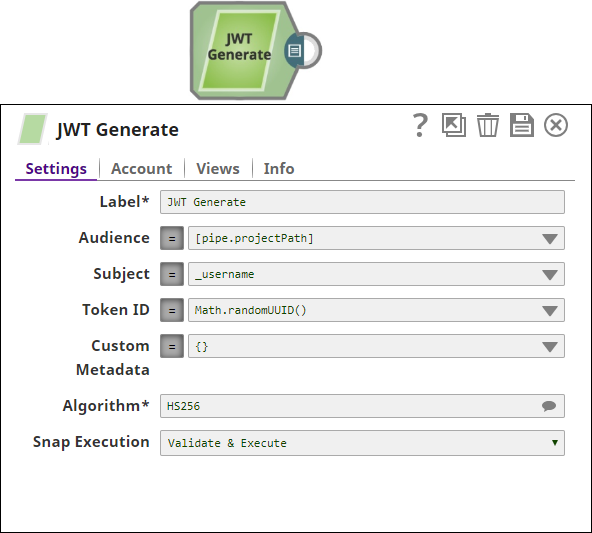
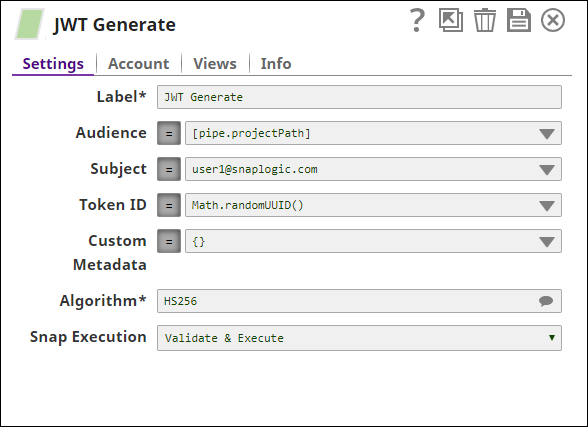
| Audience | The asset that the token should be valid for. Can be a string or a list of strings. Default value: pipe.projectPath | ||||||||||||
| Subject | The entity (user, application, etc) that this token applies to. This could be used to specify internal / third-party users or applications that the token should be valid for. Default value: [None] | ||||||||||||
| Issued At Epoch | Specify the time (in milliseconds since January 1st, 1970) that indicates when the JWT was created.
Default value: N/A. Example: 1673515370515 | ||||||||||||
| Not Before Epoch | Specify the time (in milliseconds since January 1st, 1970) before which the JWT remains invalid.
Default value: N/A. Example: 1673515370513 | ||||||||||||
| Expiration Epoch | Specify the time (in milliseconds since January 1st, 1970) after which the JWT is invalid.
Default value: N/A. Example: 1673515371515 | ||||||||||||
| Token ID | A unique identifier for the token. This field can be used to embed a unique identifier for tracking across multiple systems. Default value: Math.randomUUID() | ||||||||||||
| Custom Metadata | Custom metadata to embed in token. This field is an Object / Map. For every key value pair in this object, the key will form the name of the claim and the value will be value of the claim. Default value: [None] | ||||||||||||
| Algorithm | Required. The hashing algorithm used to generate the signature of the token. Options available include:
Default value: HS256 Alternatively, the hashing algorithm for the RSA key used to generate the signature of the token includes the following options: RS256 | ||||||||||||
| Skip Key ID | Select the checkbox (by disabling the Expression enabler) to skip the Key ID parameter and remove it when generating the JWT.
Default value: Deselected | ||||||||||||
|
| ||||||||||||
Examples
Basic Use Case
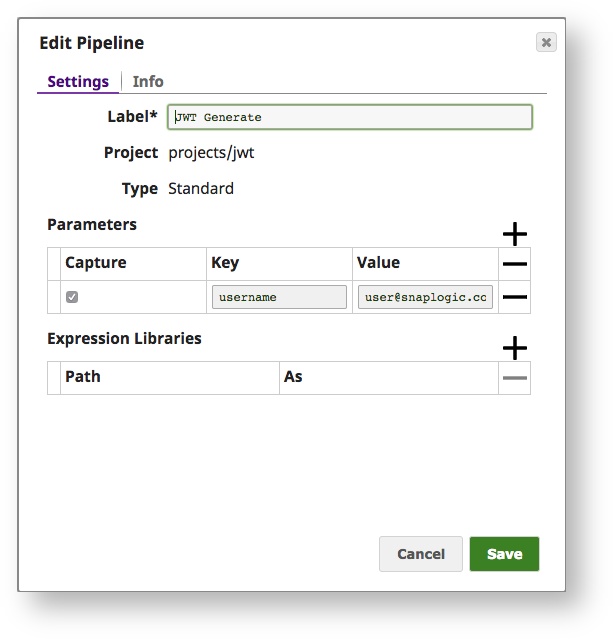
The pipeline below shows a standalone JWT Generate Snap (we define a pipeline parameter called username and there is an associated JWT Account).
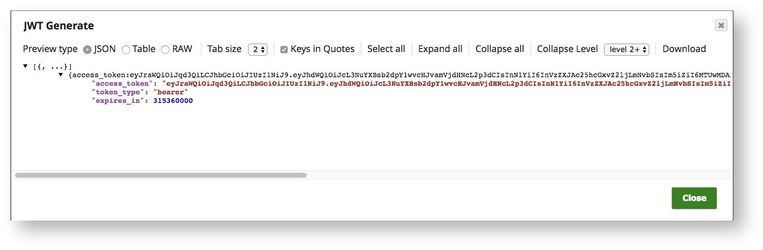
The Snap generates a JWT token as output.
Note that we're using an intentionally long token TTL for demo purposes. This is to ensure that the Validate snap can validate the token successfully.
Typical Snap Configurations
All configuration parameters (Audience, Subject, Token ID, Custom Metadata) are expressions. This provides a lot of flexibility in deciding what information gets embedded in the token. In the above example, we're using the pipeline parameter (_username) as the subject.
Advanced Use Case
The JWT Generate Snap allows users to issue limited scope tokens for internal users.
In the example pipeline below:
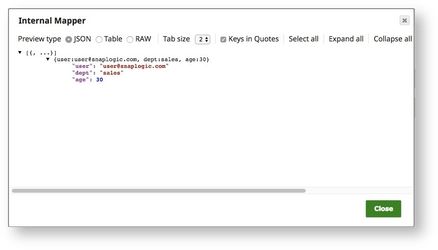
- The pipeline makes a REST Post to an internal endpoint with internal user credentials. The REST endpoint responds with JSON data associated with that user.
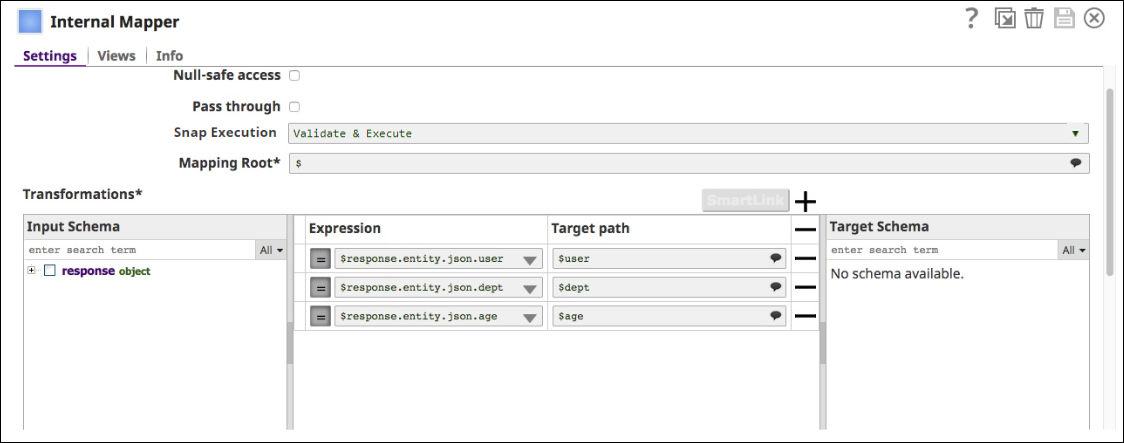
- A Mapper Snap is used to map fields that we want to embed in the token (user, dept, age in this example).
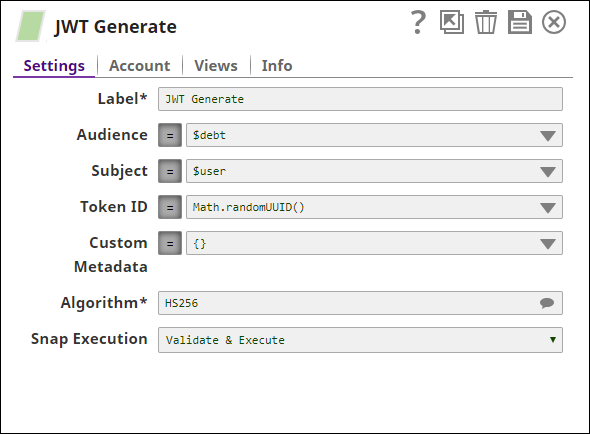
- JWT Generate Snap generates an access token that embeds this information in the token (using dept as "audience", "user" as the subject and "age" in custom metadata field).
- A Mapper is used to isolate the access token from the output document and return that access token.
- See the JWT Validate Snap documentation to see the output when this token is validated and decoded back.
Downloads
| Multiexcerpt include macro | ||||
|---|---|---|---|---|
|
| Note |
|---|
You need to create, as described in Configuring JWT Accounts to use for this sample. Use the attached jwt-keystore.jks file to create one. (The keystore was created using keytool for demo purposes. It contains one symmetric key with alias: jwt password: jwtpasswd) |
| Attachments | ||
|---|---|---|
|
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|
See Also
- SnapLogic Community: Using the DocuSign eSignature REST API with JWT authentication and REST Get Snap