In this article
| Table of Contents | ||||
|---|---|---|---|---|
|
Overview
You can use this Snap to encrypt individual field values in the input documents.
Snap Type
The Encrypt Field Snap is a Transform-type Snap.
Prerequisites
None.
Support for Ultra Pipelines
Works in Ultra Task Pipelines.
Snap Views
| Type | Format | Number of Views | Examples of Upstream and Downstream Snaps | Descirption |
|---|---|---|---|---|
Input | Document |
| Any Snap with a document output view | Stream of documents with a nested or flat map data |
Output | Document |
| Any Snap with a document input view | Same as input documents with specified field values encrypted |
Error | This Snap has at most one document error view and produces zero or more documents in the view. | |||
Account
KeyStore account or Passphrase-based Key account can used.
Use KeyStore account for X.509 key or secret (symmetric) key.
If no account is selected, the Key property should have an expression to be evaluated with the input document or the Pipeline parameter.
Snap Settings
Field | Field Type | Description | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
Label Default Value: Encrypt Field | String |
| ||||||||||
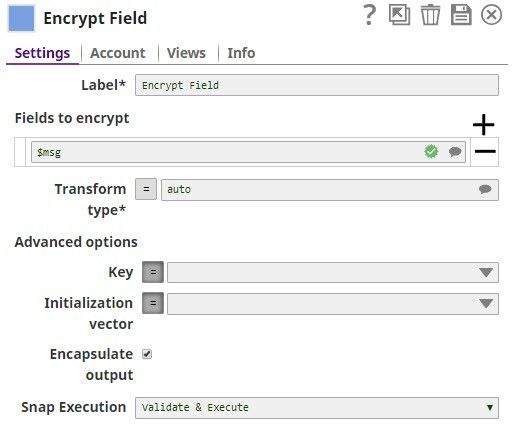
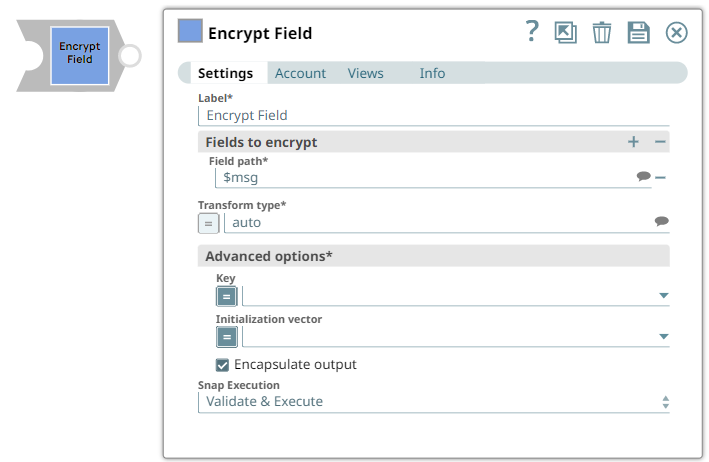
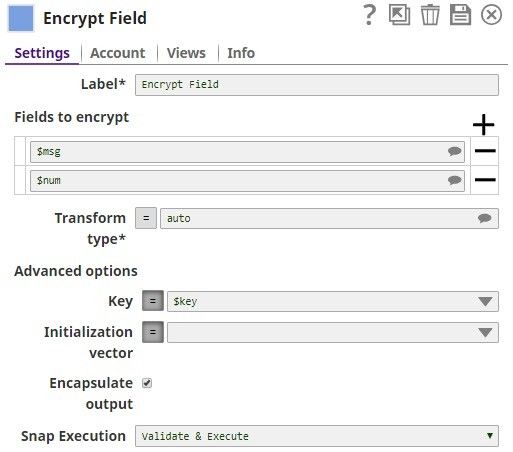
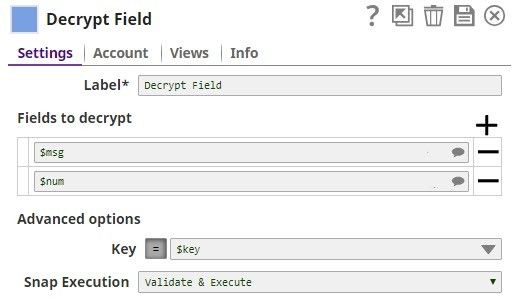
Fields to encrypt Default Value: | String | Use this field set to define the field path. | ||||||||||
Field path* Default Value: | String | A table for JSON-path expressions to fields to encrypt. Use the suggest button to select the field to encrypt. | ||||||||||
Transform type Default Value: auto
| String | The cryptographic transformation to perform, expressed as algorithm/mode/padding. Use the suggest button to select a desired transformation type. When When set to "auto", the transformation will be automatically selected based on the type of encryption key using the following table:
| ||||||||||
Advanced Options | ||||||||||||
Key Default value: None | String | Specify a JSON path or select the path by enabling the expression field that the Snap must evaluate with input document or pipeline parameter. The result must be the base64, PEM-encoded key, or non-encoded RSA public key.
Example_BINARY_Encrypt Decrypt X.509 certificate from input document.
| ||||||||||
Initialization vector Default value: None | String | JSON-path expression to be evaluated with input documents or pipeline parameters to be the base64-encoded initialization vector. Leave empty to generate one automatically. Note that the content of the initialization vector should be different for every encryption operation. Reusing IVs will make the encryption operation less secure. | ||||||||||
Encapsulate output Default Value: Selected | Checkbox | If selected, encrypted fields are JSON-encoded and encapsulated between "ENC:" and ":ENC" strings. When unselected, the field to be encrypted will be replaced with an object with the output of the encryption operation as needed to perform the decryption. | ||||||||||
Snap Execution Default Value: Vallidate & Execute | Dropdown list |
| ||||||||||
Examples
Encrypting and Decrypting Messages Using RSA Public and Private Key
The example pipeline demonstrates how to use RSA public key to encrypt messages.
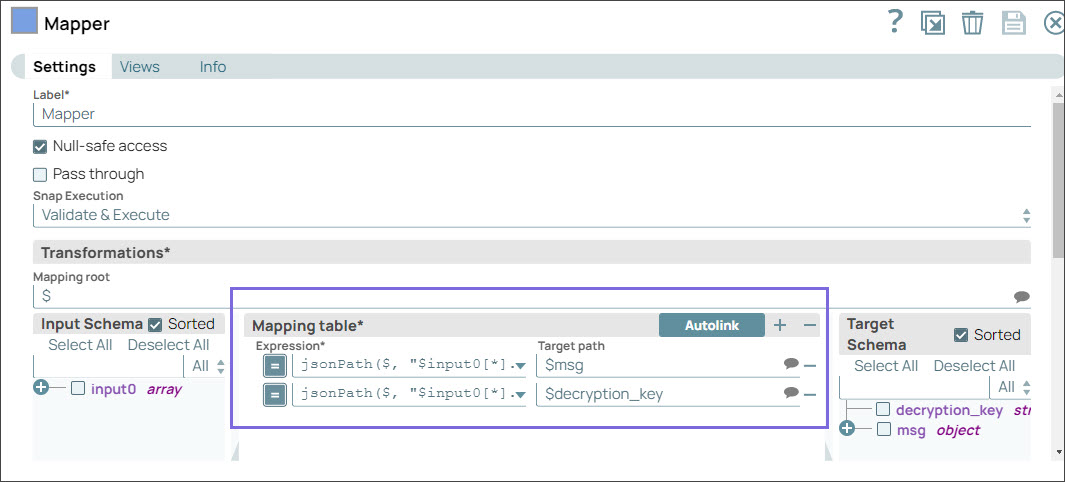
Step 1: Configure the Mapper Snap with a message that you want to encrypt and with the RSA public key.
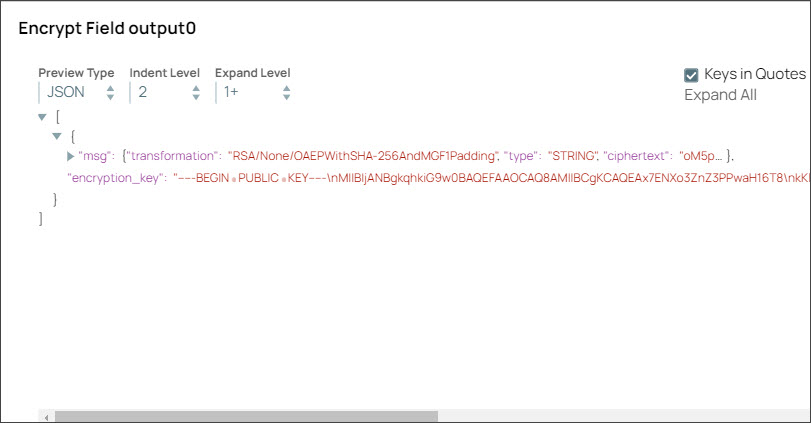
Step 2: Configure the Encrypt Field Snap with the encrypted message. On validation, the encrypted message displays in the output.
Step 3: Configure the Mapper Snap to extract the message using the decryption key, which is an RSA private key.
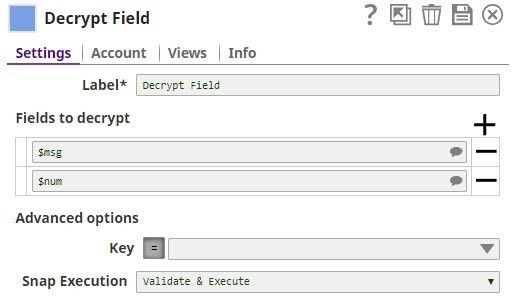
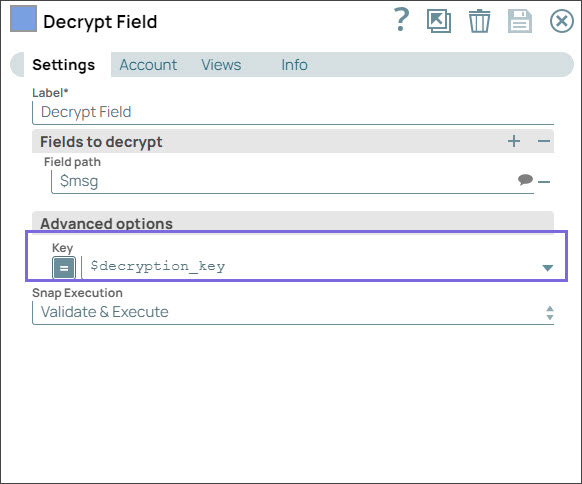
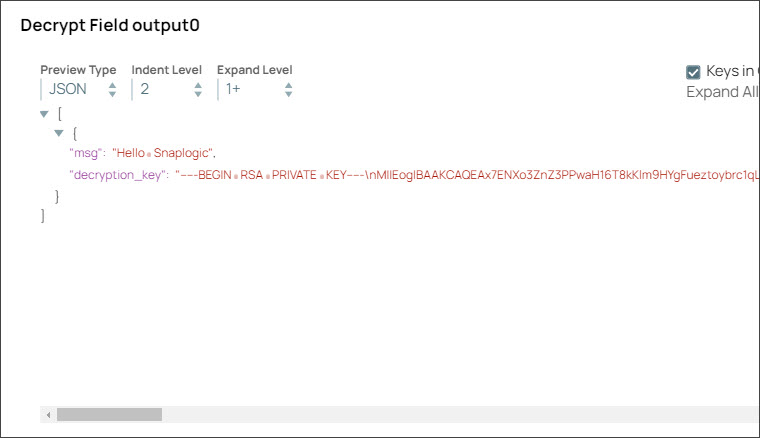
Step 4: Configure the Decrypt Field Snap with the decryption key that you pass from the upstream Mapper Snap. On validation, the Decrypt Snap displays the decrypted message in the output.
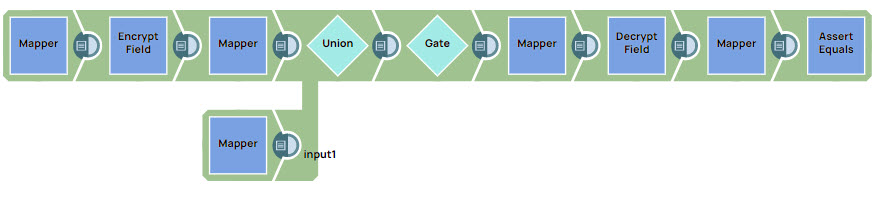
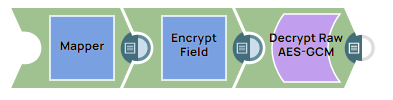
Encrypt Field Snap Without An Account: Decrypting Data With Snowflake DECRYPT_RAW Function in AES/GCM/NoPadding
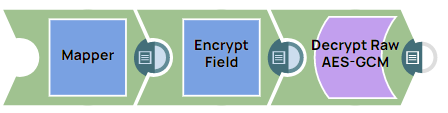
The following example Pipeline demonstrates how to decrypt data that has been encrypted by the Encrypt Field Snap (without an account) by using the Snowflake DECRYPT_RAW function.
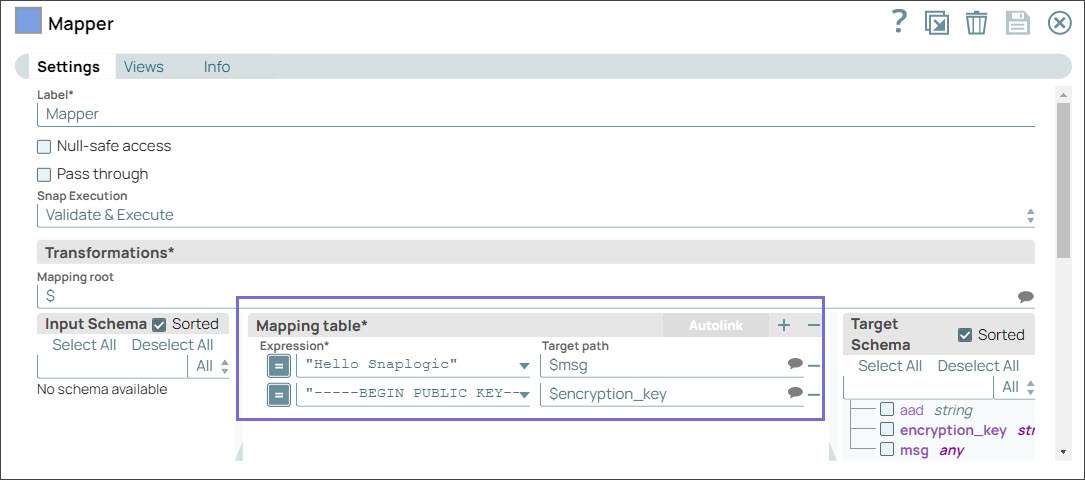
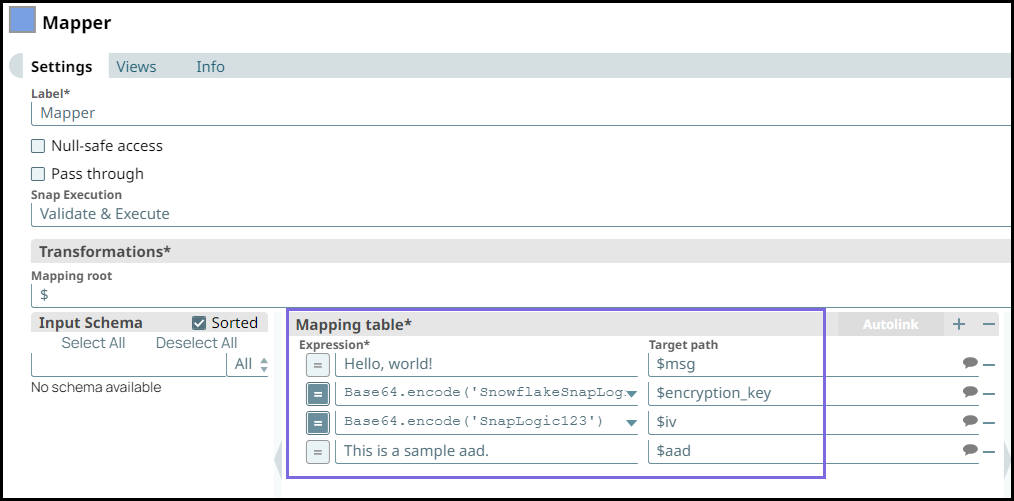
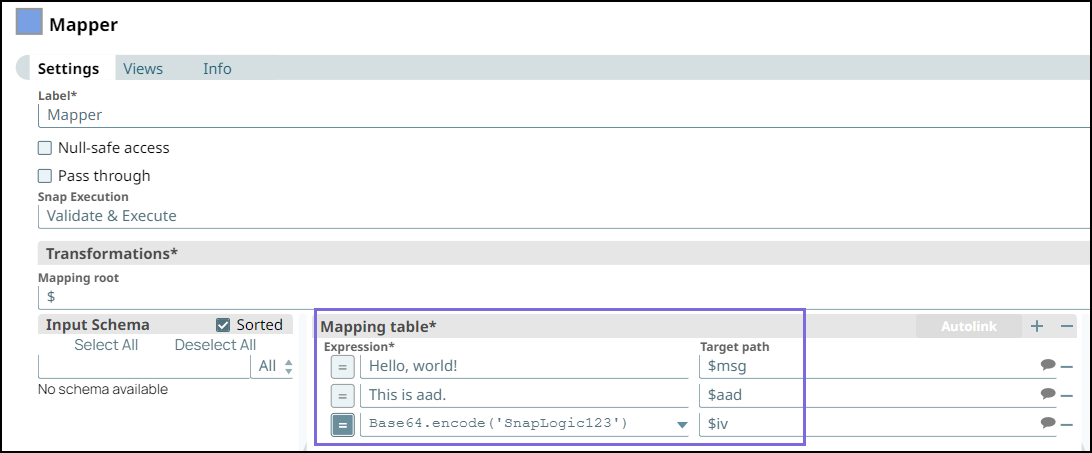
Step 1: Configure the Mapper Snap with the following data:
Enter the message
(. This is a sample message that is to be encrypted.Hello, world!)Pass an expression
Base64.encode('<passphrase>')to generate a 32 Byte encryption key. A 24-byte passphrase generates a 32-byte key. You can also pass the encryption key as a Pipeline parameter.Enter
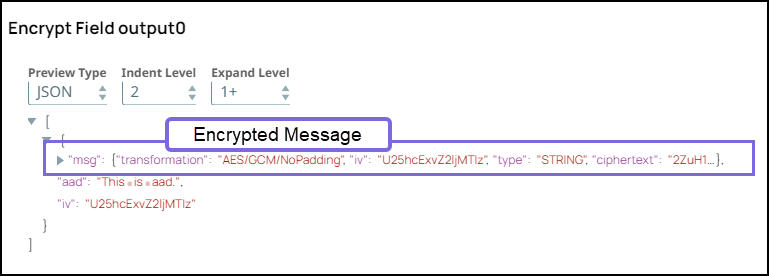
This is a sample aadin the 'aad' field, which is a required field if you intend to decrypt the data in Snowflake in AES/GCM/NoPadding. The key name ‘aad' is case-sensitive.
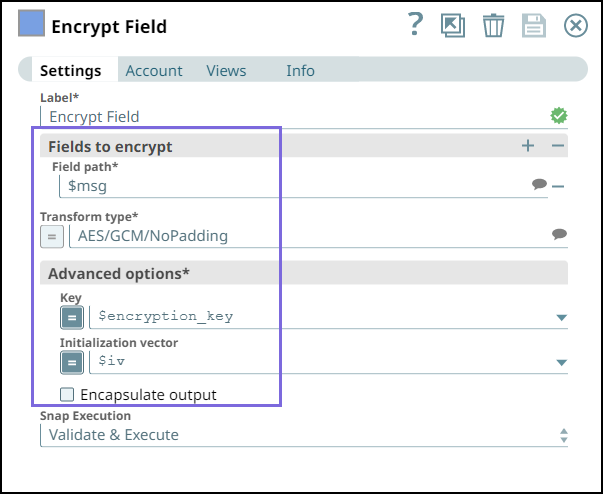
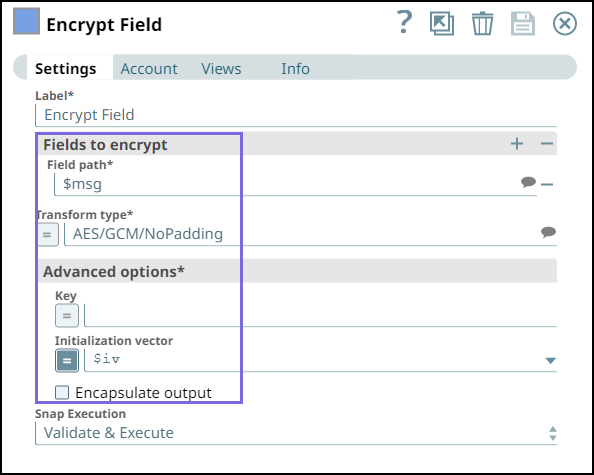
Step 2: Configure the Encrypt Field Snap as follows:
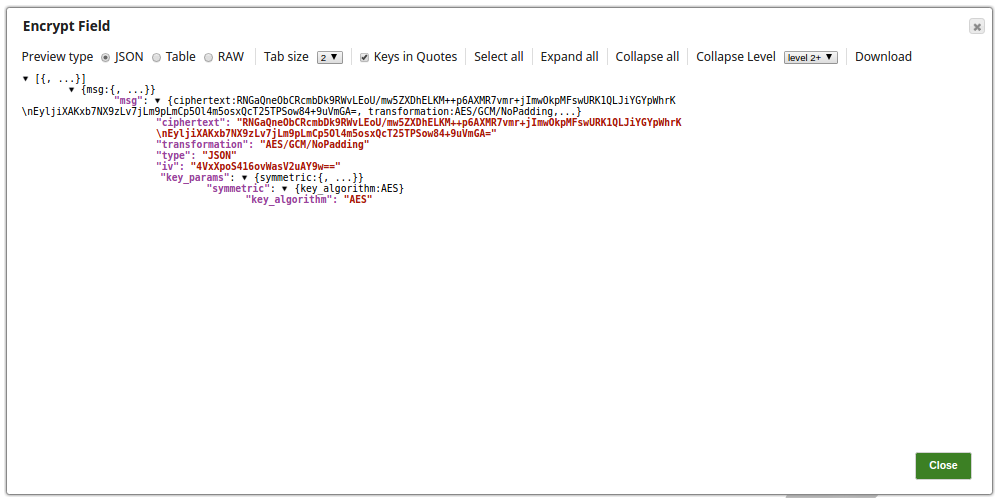
Specify $msg in the Field path. The Snap encrypts the Hello,world! message.
Select the Transform type as AES/GCM/NoPadding which is the common encryption type. The Snap transforms the message and displays it as an algorithm/mode/nopadding.
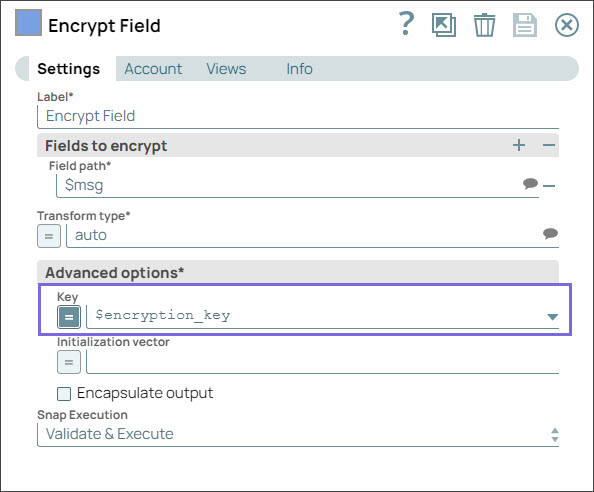
Under Advanced options specify Key as $encryption_key and Initialization vector as $iv. We do not use any account in the Encrypt Field Snap; hence, we pass an encryption key in the Key field.
Deselect Encapsulate output checkbox.
Step 3: Configure the Snowflake Execute Snap as follows:
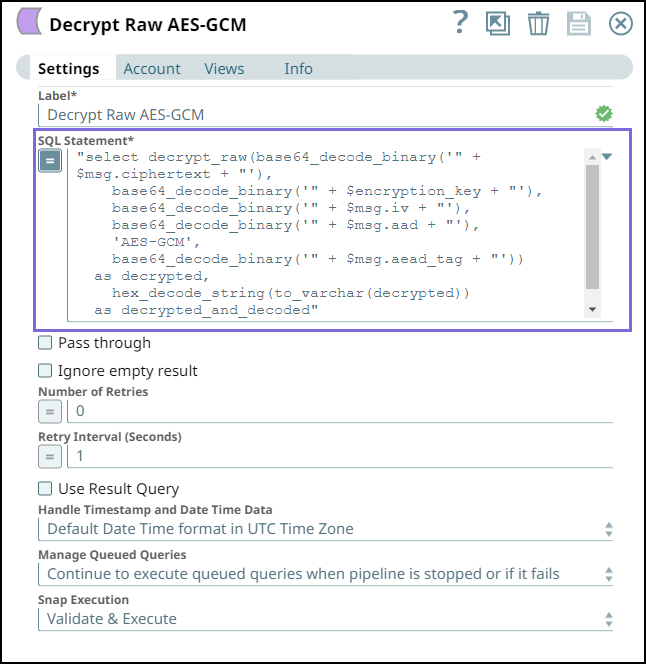
Enter the followng query with DECRYPT_RAW function in the SQL Statement field.
Paste code macro "select decrypt_raw(base64_decode_binary('" + $msg.ciphertext + "'), base64_decode_binary('" + $encryption_key + "'), base64_decode_binary('" + $msg.iv + "'), base64_decode_binary('" + $msg.aad + "'), 'AES-GCM', base64_decode_binary('" + $msg.aead_tag + "')) as decrypted, hex_decode_string(to_varchar(decrypted)) as decrypted_and_decoded"
- Use
base64_decode_binaryfunction to decode each field except for AES-GCM.
Select a valid Snowflake account for the Snowflake Execute Snap.
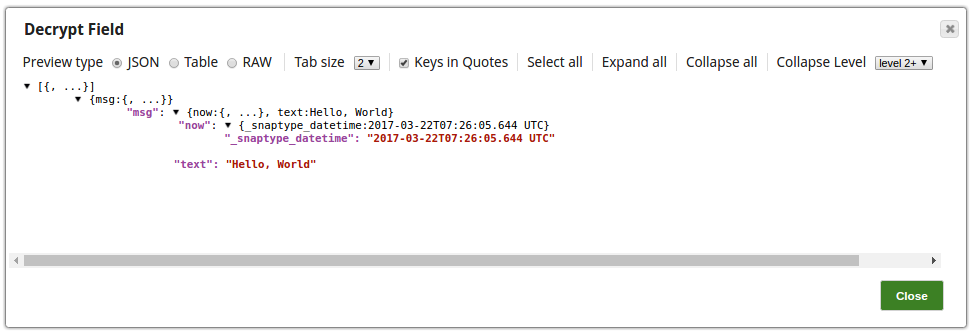
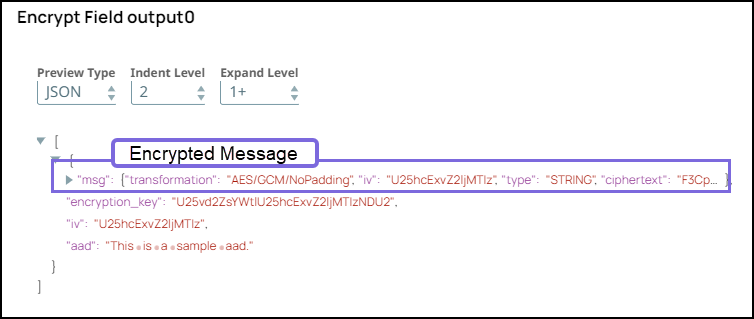
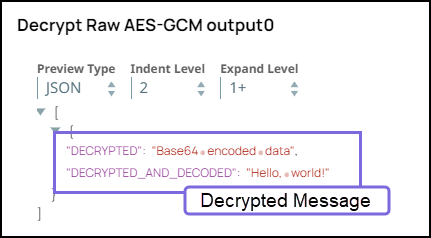
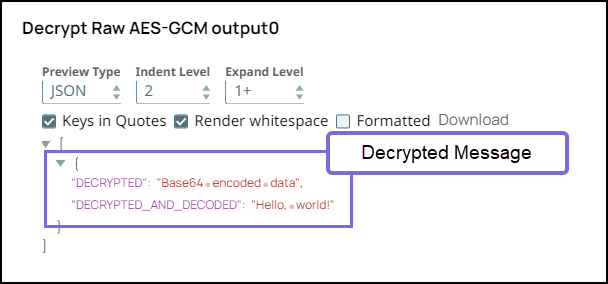
Step 4: Validate the Pipeline. Note the DECRYPTED_AND_DECODED field in the output of Snowflake Execute Snap is the same as the original message before encryption.
Encrypt Field Snap With Passphrase-based Key Account: Decrypting Data With Snowflake DECRYPT_RAW function in AES/GCM/NoPadding
The following example Pipeline demonstrates how to decrypt data which has been encrypted by Encrypt Field Snap (with Passphrase-based Key account) by using the Snowflake DECRYPT_RAW function.
Step 1: Configure the Mapper Snap with the following data:
Enter the message (
Hello, world!).Pass an expression
"Base64.encode'<passphrase>')to generate a 32 Byte encryption key. A 24-byte passphrase generates a32-byte key.You can also pass the encryption key as a Pipeline parameter.
Enter
This is a sample aadin the ‘aad’ field, which is a required field if you intend to decrypt the data in Snowflake in AES/GCM/NoPadding. The key name ‘aad' is case-sensitive.
Step 2: Configure the Encrypt Field Snap as follows:
Configure a Passprhase-based Key account as follows:
Enter “SnowflakeSnapLogic123456” in the ‘Passphrase’ field.
Enter AES in the Algorithm field.
Enter 256 in the Key Size field.
Specify $msg in the Field path. The Snap encrypts the Hello,world! message.
Select the Transform type as AES/GCM/NoPadding. The Snap transforms the message and displays it as an algorithm/mode/nopadding.
Under Advanced options leave the Key blank and specify Initialization vector as $iv.
- Deselect Encapsulate output checkbox.
Step 3: Configure the Snowflake Execute Snap with a valid Snowflake account as follows:
Enter the following query in the SQL Statement field:
Paste code macro "select decrypt_raw(base64_decode_binary('" + $msg.ciphertext + "'), sha2_binary('SnowflakeSnapLogic123456', 256), base64_decode_binary('" + $msg.iv + "'), base64_decode_binary('" + $msg.aad + "'), 'AES-GCM', base64_decode_binary('" + $msg.aead_tag + "')) as decrypted, hex_decode_string(to_varchar(decrypted)) as decrypted_and_decoded"- Use
sha2_binary('<encryption_key>', 256). For example,, 'SnowflakeSnapLogic123456' for '<encryption_key>'.
Use
base64_decode_binaryfunction to decode each field except for 'AES-GCM.'
Step 4: Validate the Pipeline. Note the DECRYPTED_AND_DECODED field in the output of Snowflake Execute Snap is the same as the original message before encryption.
| Expand | ||
|---|---|---|
| ||
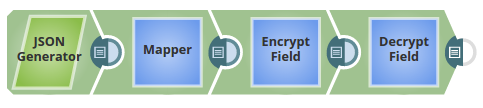
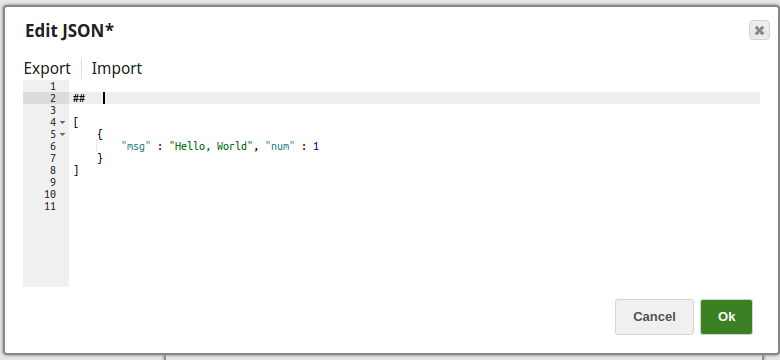
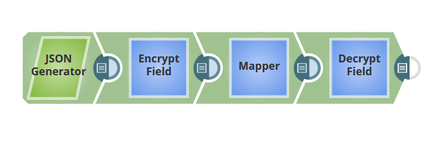
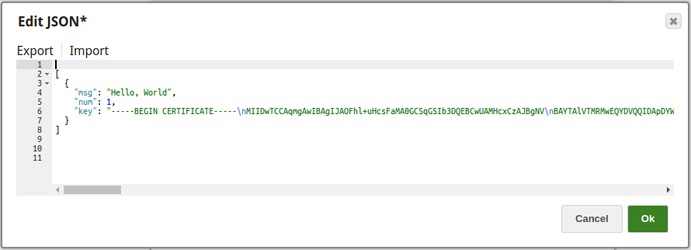
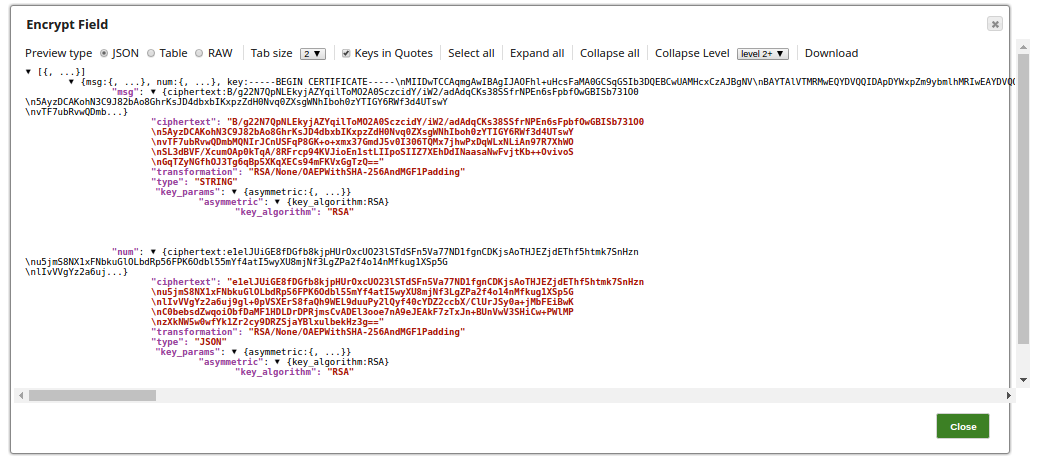
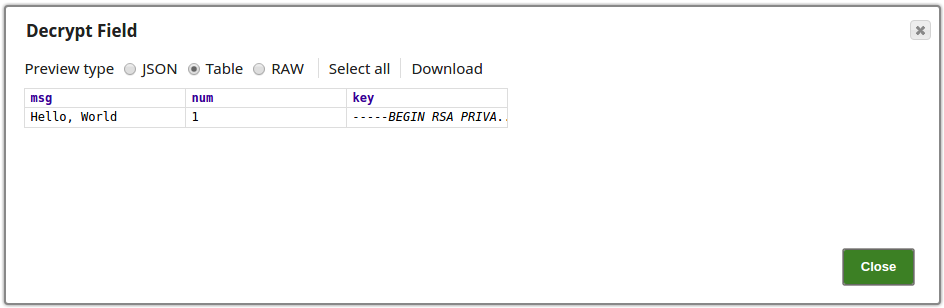
Encrypt and Decrypt Input Documents In this pipeline, the JSON Generator Snap, passes the values to the Encrypt Field Snap that provides the fields to be encrypted. The Upstream Mapper Snap maps the values to be decrypted to the Decrypt Field Snap. The JSON Generator Snap passes the values to the Encrypt Field Snap. Note that the key value is also provided. The Encrypt Field Snap provides the values to be encrypted. The key value $key is passed via the input document. The output preview from the Encrypt Field Snap: The Mapper Snap maps the values including the key value to the Decrypt Field Snap. The Decrypt Field Snap decrypts the provided fields. The output preview from the Decrypt Field Snap: |
| Expand | ||
|---|---|---|
| ||
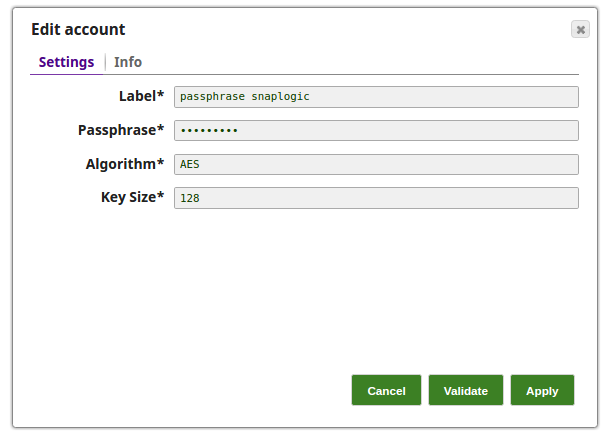
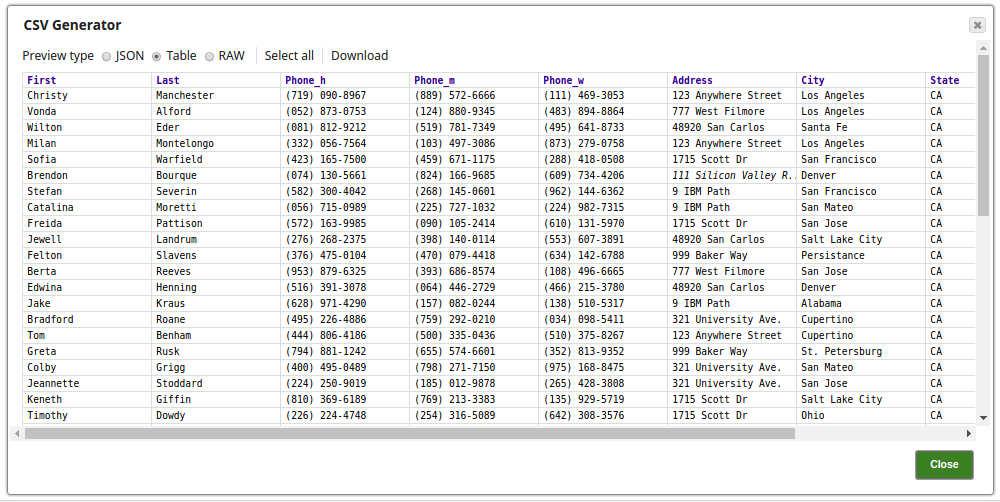
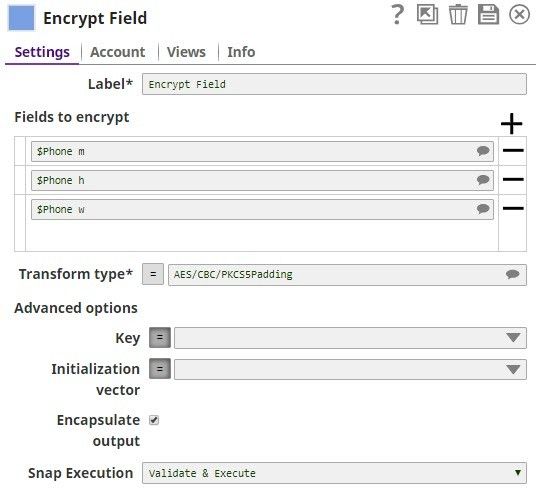
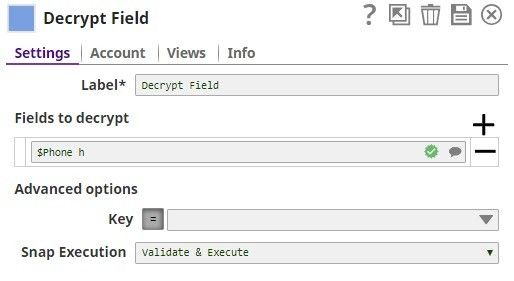
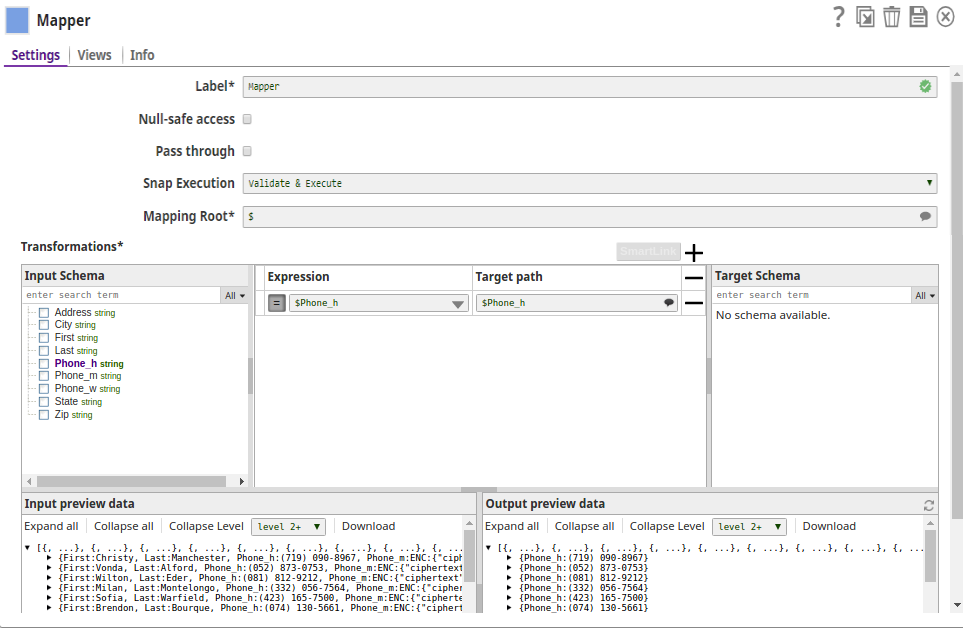
Encrypt and Decrypt Using Passphrase Account with Selected Algorithm Transform Type In this pipeline, the CSV Generator Snap supplies the values to the Field Encrypt Snap which provides the fields to be encrypted.The Decrypt Snap decrypts the fields and passes the required field values using the downstream Mapper Snap. The Snaps use the PassPhrase-based Account. The Passphrase Account set with a nine digit phrase and a key size of 128. The CSV Generator Snap passes the values to the Encrypt Snap. The Field Encrypt Snap encrypts the provided fields, $Phone_m, $Phone_h, $Phone_w. The Transform type is selected from the suggested list. The output preview from the Field Encrypt Snap: (Note the encrypted values followed by ENC:...) The Decrypt Field Snap decrypts the field, $Phone_h. Note that the output preview has the Phone_h field decrypted. The Mapper Snap passes the field $Phone_h values to the output preview: |
| Expand | ||
|---|---|---|
| ||
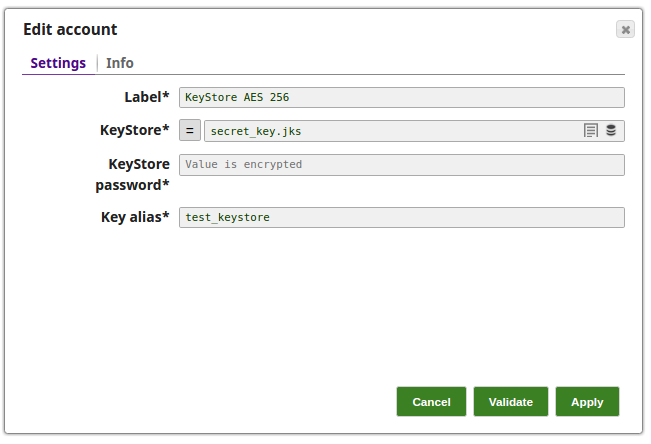
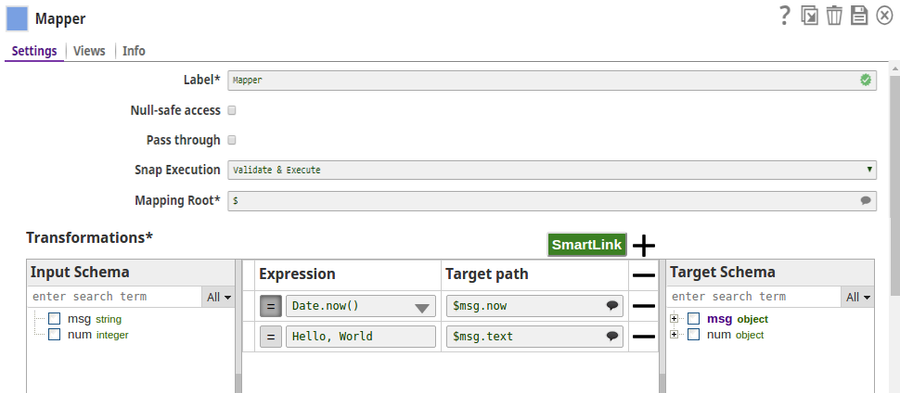
Encrypt and Decrypt Using KeyStore Account with Auto Transform Type In this pipeline, the JSON Generator Snap passes the values to the Mapper Snap that maps them to the Encrypt Field Snap for the values to be encrypted and then decrypt the values as provided in the Decrypt Field Snap. The Keystore Account set with the Keystore location as secret_key.jks. The JSON Generator Snap provides the values to the Mapper Snap. The Mapper Snap maps the values to be passed to the Encrypt Field Snap. The Encrypt Field Snap provides the fields to be encrypted. The Transform type is selected 'auto' which means that the Snap selects the algorithm as registered in the KeyStore file in the Account. The output preview from the Encrypt Field Snap: The Decrypt Field Snap decrypts the fields as provided. The successful execution of the pipeline displays the below output preview:
|
Downloads
| Multiexcerpt include macro | ||||
|---|---|---|---|---|
|
| Attachments | ||||||
|---|---|---|---|---|---|---|
|
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|
.png?version=1&modificationDate=1556774847814&cacheVersion=1&api=v2&width=900)
.png?version=1&modificationDate=1490180574671&cacheVersion=1&api=v2)
.png?version=1&modificationDate=1490180575205&cacheVersion=1&api=v2)
.png?version=1&modificationDate=1490180576661&cacheVersion=1&api=v2)
.png?version=1&modificationDate=1490180578258&cacheVersion=1&api=v2)