In this article
...
Snaps in Exchange Online Snap Pack require an OAuth2 account to access the resources in Azure. For the OAuth2 account to authorize successfully, ensure to create and configure an application corresponding to the account as displayed in the workflow.
...
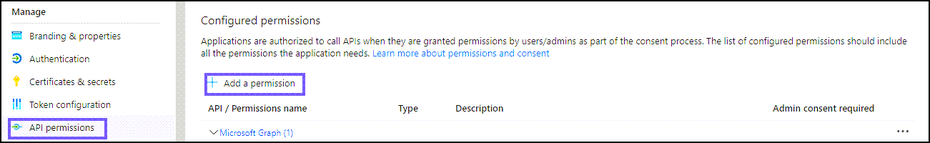
On the left navigation panel, navigate to Manage,select API permissions > Add a permission.
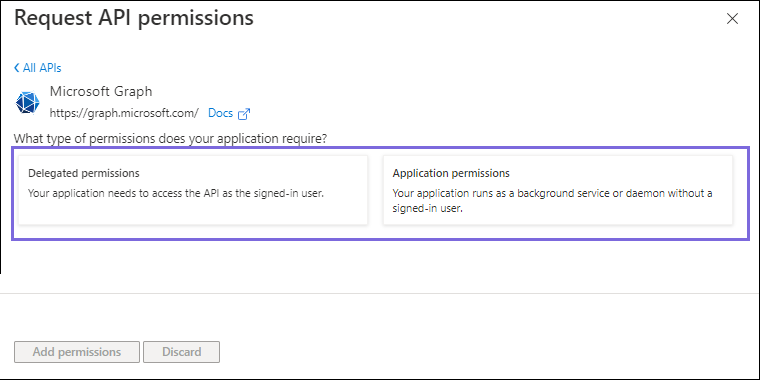
On the Request API permissions window, select Microsoft Graph > Delegated permissions and Application permissions for the OAuth2 Account.
Select the permissions from Files, Users, and Teams. Choose the minimum and mandatory API permissions listed under Scopes and Permissions.
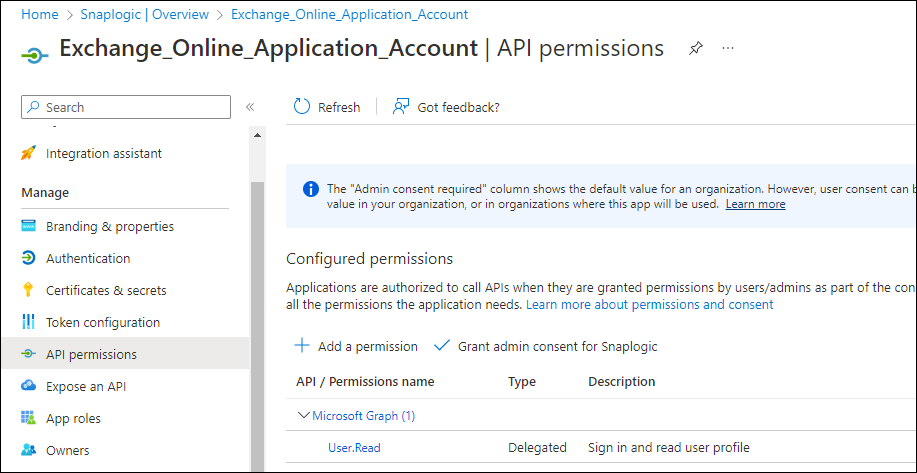
Click Add Permissions. View all the permissions added under Configured permissions.
Click Grant admin consent confirmation and select Yes.
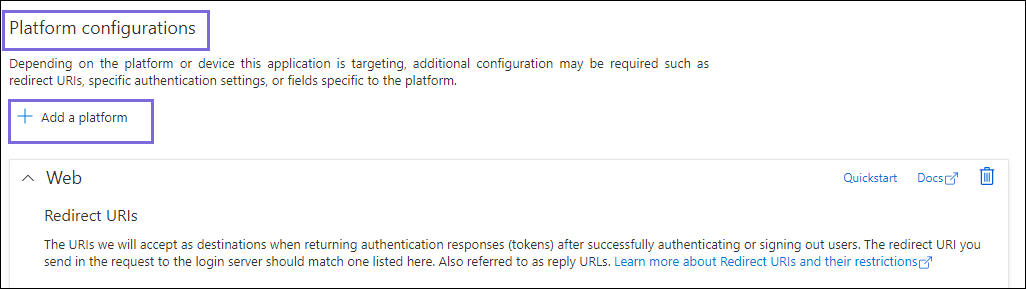
Click Overview, and select Add a Redirect URI. You will be redirected to the Platform configurations page.
Under Platform configurations, click Add a platform.
Select Web and specify either of the following Redirect URIs based on the region your server is located:
https://emea.snaplogic.com/api/1/rest/admin/oauth2callback/exchangeonlinehttps://elastic.snaplogic.com/api/1/rest/admin/oauth2callback/exchangeonlineClick Configure. A popup message displays which indicates that the application is successfully updated.
On the Platform configurations page, click Save. The Redirect URIs are added the to the application.
Locate Application credentials in the Azure Portal
...
Delegated permissions (User account only*) | |||
|---|---|---|---|
Permission | Display String | Description | Admin Consent Required? |
offline_access (Mandatory for Autorefresh token.) | offline_access | offline_access must be selected in the case you use the Auto-refresh token option. | Yes |
Application permissions | |||
Permission | Display String | Description | Admin Consent Required? |
User.Read.All | User.Read.All | This permission allows the application to read the full set of profile properties, reports, and managers of other users in your organization, on behalf of the signed-in user. | Yes |
...