...
Starting the Snaplex for the first time automatically generates the data keys. The keys need to be manually synced across the Groundplex nodes. The account data encryption keys are located in the /etc/snaplogic directory. The jcc-datakeys.jks file is the keystore and the jcc-datakeys.pass is the password for the keystore. The same set of keys should be used on all the Groundplexes nodes , across the whole Org.
For TLS connections, the Snaplex also maintains SSL certificates. These are also in the /etc/snaplogic directory, the jcc-serverkeys.jks file is the keystore and jcc-serverkeys.pass is the password for the keystore. These should be unique for each node and, and therefore, should not be synced across the Groundplex nodes. The certificates are not used for account encryption ; they are but for TLS connections only.
...
All Accounts are sent to the Groundplex to be decrypted with the old key and encrypted with the new key.
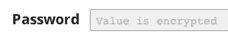
Encrypted Account fields do not display values, as shown below. However, you can change the value by entering and saving a new one and saving it.
If an Org admin changes the encryption sensitivity level from Low, Medium, High to High, existing accounts remain at the previous level unless you update them. Changing from High to Low, Medium, High causes account data to be encrypted. All new Accounts follow the updated sensitivity encryption level.
If The encrypted data is not automatically decrypted if you revert from Enhanced to Standard encryption, the encrypted data is not automatically decrypted. As . The encrypted values continue to work as long as the server key is still in the node, the encrypted values continue to work.
Accounts that were exported when the Org used the old key have the sensitive fields encrypted with the old key. When an Account is imported into the Org after the key is rotated, it is imported with the old key. To convert these imported accounts to the new key, go to Manager and redo the key rotation with the new key.
...
Make backup copies of the generated data keystore and password files. Otherwise, if the data keys become corrupted and are unrecoverable, to recover connectivity, you would have to must manually re-enter all sensitive Account field values manuallyto recover connectivity.
Do not change an Org that uses Enhanced Encryption back to Standard Encryption. If you do so, existing OAuth 2.0 accounts will not function; you will need to must re-create them.
Prerequisites
...
Find the
jcc-datakeys.jksandjcc-datakeys.passin the/etc/snaplogicfolder of the Linux machine.Copy the data key files to a directory on the Windows machine that only security administrators and users running the Snaplex node can access.
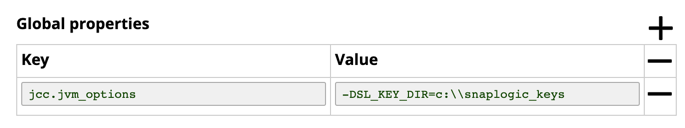
Add the directory name , as the value of a new
SL_KEY_DIRJava property in the Snaplex configuration file:Navigate to the target Snaplex in Manager , and click to open it.
Click the Node Properties tab, and under Global Properties, click
to enter the key-value pair.
Add the following in the Snaplex property, where Value is the location of the data keys. For example:
Click Update.
Restart the SnapLogic service on all nodes with the updated
slpropzconfiguration.
...
When you view the Org Settings, the new Status displays status is displayed under Configure Encryption with the following fields:
| Groundplex processing status |
|---|---|
Status | Indicates if the Groundplex processing has been successfully executed without encountering errors or issues. |
Description | The number of accounts encrypted and processed out of the total number of accounts. |
Last Update | The timestamp of the last update or completion of the Groundplex processing operation. |
Rotating Private Keys
To rotate the Enhanced Encryption key, follow these steps:
Install the latest Snaplex RPM/DEB installation package on one of the Groundplex nodes that is already using Enhanced Encryption. This step is required to get the new addDataKey option in the
jcc.shscript.As the root user, run the following command. This command generates a new key pair and appends it to the keystore in the
/etc/snaplogicfolder with the specified alias. In the example, the alias iskeyFeb2020:Code Block /opt/snaplogic/bin/jcc.sh addDataKey keyFeb2020
Copy the generated data keys files (
jcc-datakeys.jksandjcc-datakeys.pass) from this node to all the others for the Snaplex, similar to when originally setting up Enhanced Encryption.Restart the nodes. This step is required to pick up the updated key pair. To do an online restart, use the Snaplex restart option in the Dashboard.
When all nodes are running run with the new key pair, the Enhanced Encryption settings display the drop-down list, allowing the Org admin to change to the new key.
...
When you add nodes to a self-managed Snaplex, the new nodes must have the same encryption key as the other nodesothers. If the new node does not have a matching key, it is ignored until the keys are synchronized and the JCC is restarted. The All nodes' current configuration for all the nodes can be checked in Manager > Settings > Configure Encryption.
Special Use Case: Adding Linux Nodes to an Org Where Keys Were Generated on a Windows Node
To The recommended procedure to enable Enhanced Encryption on Windows Groundplex instances , the recommended procedure is to generate the keys on a Linux machine and then copy them onto the Windows node. The advantage is that the generated keystore is encrypted, and the same keystore can be used on both Windows and Linux nodes.
...