On this page
Overview
You can create an account with the Designer or Manager. In Designer, when working on pipelines, every Snap that needs an account prompts you to create a new account or use an existing account. The accounts can be created in or used from:
- Your private project folder: This folder contains the pipelines that will use the account.
- Your Project Space’s shared folder: This folder is accessible to all the users that belong to the Project Space.
- The global shared folder: This folder is accessible to all the users within an organization in the SnapLogic instance.
Prerequisites
Valid permissions based on the Snap and intended operation. See the Account Permissions the section below for more information.
Account Settings
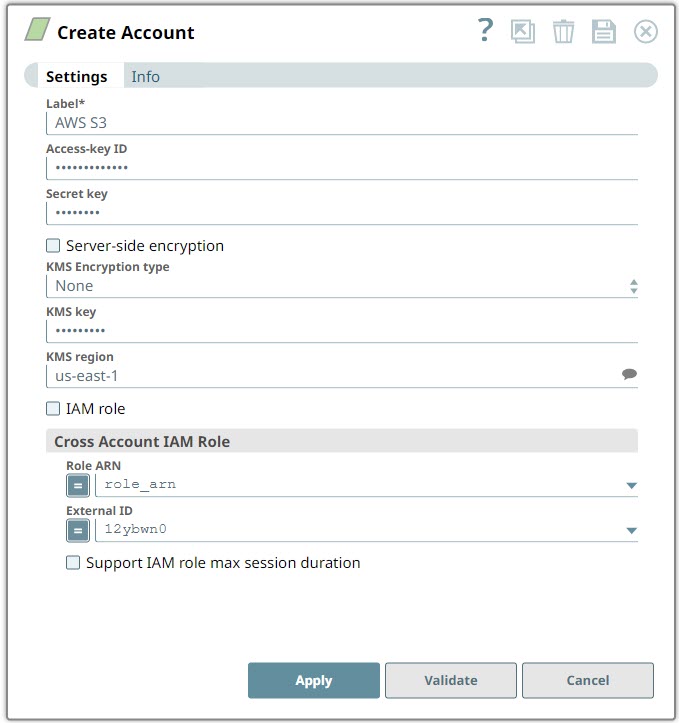
Label | Required. User-provided label for the account instance | |
|---|---|---|
Access-key ID | Required when the IAM role is disabled. Unique access key ID part of AWS authentication. Default value: [None] | |
Secret key | Required when the IAM role is disabled. The secret key part of AWS authentication Default value: [None] | |
| Server-side encryption | If selected, the S3 file is written and encrypted using the 256-bit Advanced Encryption Standard AAES256. For Snaps that read objects from S3, this field is not required, as encrypted data is automatically decrypted when data is read from S3. Default value: Not Selected | |
| KMS Encryption type | This field represents the AWS Key Management Service key used to encrypt S3 objects. It can be the key ID or ARN. For Snaps that write objects to S3, this is required for encryption types Server-Side encryption with AWS KMS-Managed Keys and Client-Side encryption with AWS KMS-Managed Keys. For Server-Side encryption, the key must be in the same region as the S3 bucket. For Client-Side encryption, a key from any region can be used by using the key ARN value. If a key ID is used for Client-Side encryption, it defaults to the us-east-1 region. For Snaps that read objects from S3, this field is not required. The available options are:
Default value: [None] | |
| KMS key | Specifies the AWS Key Management Service (KMS) key ID or ARN to be used for the S3 encryption. This is only required if the KMS Encryption type property is configured to use the encryption with KMS. For more information about the KMS key refer to AWS KMS Overview and Using Server Side Encryption. For Snaps that write objects to S3, this is required for encryption types Server-Side encryption with AWS KMS-Managed Keys and Client-Side encryption with AWS KMS-Managed Keys. For Server-Side encryption, the key must be in the same region as the S3 bucket. For Client-Side encryption, a key from any region can be used by using the key ARN value. If a key ID is used for Client-Side encryption, it defaults to the us-east-1 region. For Snaps that read objects from S3, this field is not required. Default value: [None] | |
| KMS region | Name of the region to which the KMS key belongs. Example: s3.us-east-2 | |
| IAM role | If selected, the IAM role stored in the EC2 instance is used, instead of the normal AWS authentication, to access the S3 bucket. The Access-key ID and Secret key fields are ignored in this case. To create EC2 role, see Configuring an EC2 role for IAM Role in AWS S3 Account.
| |
| Cross Account IAM Role | This field set helps in granting cross account access, with two fields:
These fields helps you in setting up Cross Account IAM Role. | |
| Role ARN | The Amazon Resource Name of the role to assume. Default value: [None] | |
| External ID | An optional external ID that might be required by the role to assume. Default value: [None] | |
Support IAM role max session duration | Select this checkbox when you want to extend the maximum session duration of an IAM role defined in AWS. On selecting this checkbox, the cross-account IAM role is assumed with the maximum session duration defined for the IAM role. Default Value: Deselected | |
Account Encryption
| Standard Encryption | If you are using Standard Encryption, the High sensitivity settings under Enhanced Encryption are followed. | |
|---|---|---|
| Enhanced Encryption | If you have the Enhanced Account Encryption feature, the following describes which fields are encrypted for each sensitivity level selected per each account.
| |
Account Permissions
| Snap | Snap Operation | Minimum S3 Permissions |
|---|---|---|
| S3 Account |
| s3:ListAllMyBuckets |
| S3 File Writer |
| s3:PutObject |
| s3:PutObject, s3:ListBucket | |
Write object tags. | s3:PutObject, s3:PutObjectTagging | |
Update the Access Control List (ACL). | s3:PutObject, s3:ListAllMyBuckets, s3:PutObjectAcl | |
Suggest list of buckets in the File name field. | s3:ListAllMyBuckets | |
Suggest S3 objects in File name field. | s3:ListBucket | |
| S3 File Reader | Read files. | s3:GetObject |
| Read versioning-enabled files. | s3:GetObject, s3:GetObjectVersion | |
| Suggest list of buckets in the File field. | s3:ListAllMyBuckets | |
| Suggest S3 objects in the File field. | s3:ListBucket | |
| Suggest list of Version IDs. | s3:ListBucketVersions | |
| Read object tags. | s3:GetObject, s3:GetObjectTagging | |
| File Writer |
| s3:PutObject |
| s3:PutObject, s3:ListBucket | |
| ZipFile Writer | Write file with 'File action'=OVERWRITE. | s3:PutObject |
| Write file with 'File action'=IGNORE or ERROR. | s3:PutObject, s3:ListBucket | |
| File Reader | Read files. | s3:GetObject |
| ZipFile Reader | Read files. | s3:GetObject |
| Multi File Reader | Read one file only without wildcards. | s3:GetObject |
| s3:GetObject, s3:ListBucket | |
| Directory Browser | List files and directories. | s3:ListBucket |
| File Delete | Delete files. | s3:DeleteObject, s3:ListBucket |
| File Operation | Copy files. | s3:GetObject, s3:PutObject, s3:ListBucket |
| Move files. | s3:GetObject, s3:PutObject, s3:ListBucket, s3:DeleteObject | |
| File Poller | Poll files. | s3:ListBucket |
See Setting Permissions and Permissions for the Amazon S3 Bucket for more information.
ACL permissions
| ACL permission | Corresponding access policy permissions when the ACL permission is granted on a bucket | Corresponding access policy permissions when the ACL permission is granted on an object |
|---|---|---|
READ | s3:ListBucket, s3:ListBucketVersions, and s3:ListBucketMultipartUploads | s3:GetObject and s3:GetObjectVersion |
WRITE |
In addition, when the grantee is the bucket owner, granting | Not applicable. |
READ_ACP | s3:GetBucketAcl | s3:GetObjectAcl and s3:GetObjectVersionAcl |
WRITE_ACP | s3:PutBucketAcl | s3:PutObjectAcl and s3:PutObjectVersionAcl |
FULL_CONTROL | Equivalent to granting READ, WRITE, READ_ACP, and WRITE_ACP ACL permissions. Accordingly, this ACL permission maps to a combination of corresponding access policy permissions. | Equivalent to granting READ, READ_ACP, and WRITE_ACP ACL permissions. Accordingly, this ACL permission maps to a combination of corresponding access policy permissions. |