On this page
| Table of Contents | ||||
|---|---|---|---|---|
|
...
Single Sign On is a convenient way for users to log into multiple services without needing to enter their user name username and password for each service. SnapLogic supports Single Sign On (SSO) through the Security Assertion Markup Language (SAML) standard. If you are using a SAML-2 compatible Identity Provider (IdP) to perform SAML authentication, then you can configure your SnapLogic organization to authenticate users against your IdP.SnapLogic certified authentication methods are. If you disable password-based login, users will have to use SSO. If you leave password-based login enabled, users can choose basic authentication or SSO to log in.
SnapLogic certifies the following IdPs as compatible with our platform:
- OpenAM
- Microsoft Azure Active Directory (AD)
- OKTA
- Ping
...
- Entra ID
- Okta
- Ping
| Info |
|---|
If your organization has multiple SnapLogic environments (Orgs), they must all be configured to use the same IdP Application Integration. Members of an SSO-enabled Org might need to log into a different Org, such as one provided by SnapLogic for training or product trials. In this case, the account in the Org without SSO should be created using a different email address. |
SAML Overview
The SAML standard defines how Service Providers (SP) can , in this case, the SnapLogic Platform, communicate with Identity Providers (IdP) to securely authenticate users. In this case, SnapLogic is the Service Provider and OpenAM is the Identity Provider. The communication between the two starts after the user enters their organization name and clicks the SSO Log In button on the SnapLogic home page. The SnapLogic server uses the organization name to find the associated IdP and then redirect the user's web browser to that IdP with an authentication request. The destination for the redirect is defined by the IdP metadata file that is uploaded when configuring the user's organization to use SSO.
After the IdP receives the authentication request, it validates the request to ensure it is coming from a known Service Provider (SP) and then redirects the users browser back to SnapLogic. The IdP is informed of the SnapLogic service by uploading the SnapLogic metadata file that is generated when configuring the user's organization to use SSO. Finally, the authentication response is validated by the SnapLogic server using the IdP metadata and the user is allowed to begin working in the SnapLogic Designer.
Configuration
As mentioned in the SAML Overview section, configuring your organization to use SSO requires the exchange of metadata between the SP and the Identity Provider (IdP). You must first create an application integration in your IdP that will handle authorization for all of your SnapLogic Orgs. After you create the application integration in your IdP, export the metadata and import it into all of your SnapLogic Orgs using Classic Manager or Admin Manager.
The communication between the SnapLogic Platform and the IdP starts after the user clicks the Single Sign On link from the SnapLogic login screen. The user enters an Org name and clicks Log in. The request destination is defined in the SSO configuration. The SnapLogic Platform sends a SAML request to the IdP application integration that you created for SnapLogic. The request contains an AssertionConsumerServiceURL element that specifies where the response should be sent. The IdP ensures that the AssertionConsumerServiceURL is associated with the requester. To make this possible, you must add the Reply URLs for all of your SnapLogic Orgs to the IdP application integration.
Configuration
Configuration takes place in both your IdP and in the SnapLogic Platform. You must have Org admin access to configure SSO. To perform this exchange:
...
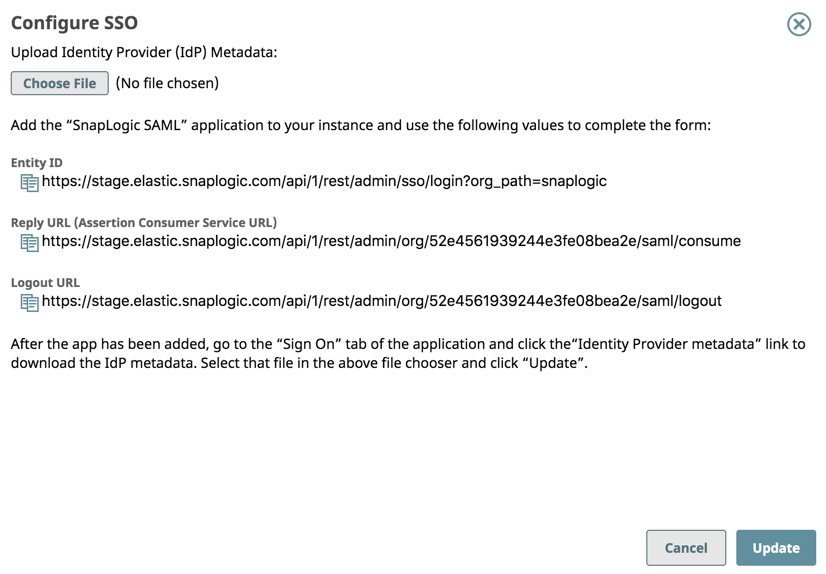
- Entity ID: Click to copy and paste this URL in the SAML entity field of your IdP.
- Reply URL: Click to copy and paste this URL in the SAML token field of your IdP.
- Logout URL: Click to copy and paste this URL in the SAML Logout response field of your IdP.
...
The main steps include:
- Create an IdP application integration for SnapLogic. Some IdPs call this an Application, others an app integration.
- Configure your SnapLogic Orgs
Create an IdP Application Integration
If your company has multiple SnapLogic Orgs, use the metadata from one Org to set up one IdP Application Integration.
- Choose one of your SnapLogic Orgs to provide the metadata for the IdP Application Integration. It doesn't matter which Org you choose, however, any user who wants to use SSO to sign in must be a member of this Org.
- Log into that SnapLogic Org and do the following:
- Click Configure SSO. The dialog opens.
- Copy the Entity ID, Reply URL, and Logout URL to a text file. You will need them when creating your IdP application integration. Note that your IdP might use a different name for these URLs. For example, the SnapLogic Reply URL value goes into the Okta Single sign-on URL field.
- Click Configure SSO. The dialog opens.
- Log into the remaining SnapLogic Orgs and do the following:
- Click Configure SSO. The dialog opens.
- Copy the Reply URL to a text file that you created in Step 2b. Note that the Reply URL contains the Org ID, not the Org name.
- Log into your IdP and create one application integration for SnapLogic access:
- Provide the Entity ID, Reply URL, and Logout URL for the Org that you chose in step 1.
- Provide the Reply URLs that you copied in step 3b to the list of Reply URLs in the IdP’s application integration
- Export the metadata from the IdP application integration. In some IdPs, such as Okta, provide a URL instead of a download button. You can open the URL in a new browser tab to view and save the XML.
- Save the exported metadata on your machine to use when configuring your SnapLogic Orgs.
Configure SnapLogic Orgs
Use the metadata from the IdP Application Integration for SnapLogic to configure SSO on all of your Orgs.
- Log into the Org you used to provide the Entity ID, Reply URL, and Logout URL for the IdP Application Integration.
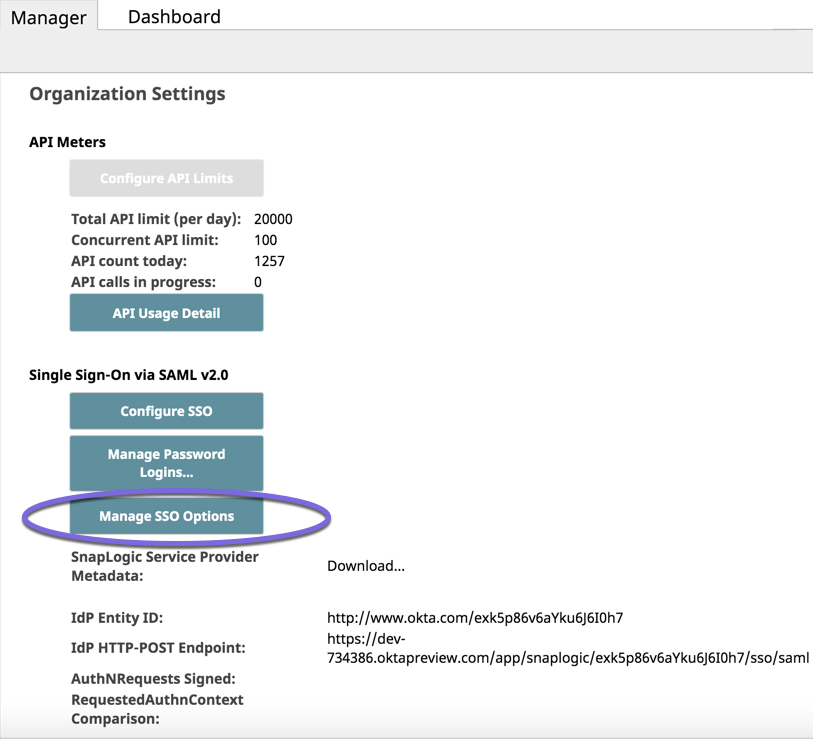
- In SnapLogic Manager, click Settings in the main menu on the left. The Organization Settings page opens.
- Scroll down and click Configure SSO.
- Click Choose File and navigate to the metadata file from your IdP that you saved previously.
Click Update to upload the metadata.
When the upload finishes, the SnapLogic server validates the metadata and updates the Settings page to reflect the new values.Note Double-check the values to ensure that they refer to your IdP.
- The Settings page offers a download link adjacent to the SnapLogic Service Provider Metadata row. Click this link to download the metadata to your machine.
- Go to the IdP's console and perform the applicable steps to upload this metadata. At this point, everything should be configured and ready for use.
...
| title | Using One IdP Metadata File across Multiple Orgs |
|---|
...
- Repeat Steps 2 -5 for all Orgs.
Manage SSO Options
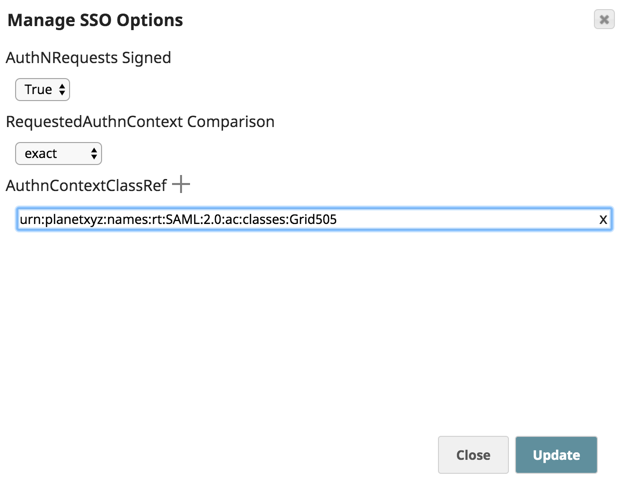
You can customize the the SSO login with additional authentication at the Org level using the Manage SSO Options feature. This feature enables you to configure AuthnRequest, RequestedAuthN Context Comparison, and AuthNContextClassRef authentication methods after uploading the IdP metadata file.
...
- Go to SnapLogic Manager, and click Manage SSO Options.
- Choose additional authentication options for the SnapLogic users in your Org as appropriate:
- AuthNRequests Signed: Select True to authenticate the sign-on against a 3rd-party entity. Selecting False declines this authentication method. The default setting is False.
- RequestedAuthN Context Comparisons: Select the method (exact, minimum, maximum, better). The default setting is exact.
- AuthnContextClassRef: Click to enter the context class references as values.
Click Update.
Info We recommend that you have at least one admin user with a password login to unlock locked accounts. For example, accounts that are created before applying the SSO login to an Org, might get locked. In such cases, you can use the admin account with a password to log in and unlock the accounts.
Adding Users
After configuring your SnapLogic organization to authenticate via SSO, the organization administrator still needs to add users to the organization to authorize them to use the SnapLogic service. Adding users can be done through the 'Users' page in the Manager.
| Note |
|---|
When creating users, you can select Disable password-based login to create the user in the system but not give then access through SnapLogic's login if you want to force them to use SSO to log in. |
Logging In
To log in using SSO, navigate to the SnapLogic login page, click Login via Single Sign On. Enter your organization the Org name and then click Log In. The login sequence should first redirect your web browser to the IdP login page and then to the SnapLogic Designer. If the SnapLogic server detects any errors during login, they are displayed below the login form on the SnapLogic home page.
Users In Multiple Organizations
...
| Note | ||
|---|---|---|
| ||
We support case-sensitive Org names. As a user, make sure that your Org name matches that of your organization in the User Name field of the login page. For example, if the organization name is SnapLogic, then do NOT use Snaplogic as your Organization. |
Users In Multiple Orgs
When SSO is enabled, users have access to all Orgs where they have an account. For example, if a user is a member of Org_1 and Org_2 and they log into Org_1 with SSO, they can switch to Org_2 without logging in again. This is assuming that both Orgs have the same IDP provider configured. If that is not the case, they receive a message stating SSO login cannot be used for users that are members of orgs that have different identity providers. The authentication process only validates that the person logging into the service is who she they say she isthey are; it does not control what she has access they have access to.
Manage Password Logins
...
You can give users a choice of using SSO or a password. If you want all users to log in with SSO, password login must be disabled.
To disable password login after you configure SSO, in Classic Manager:
- Click Settings from the left navigation bar.
- Scroll down and click the Manage Password Logins button
...
- under Single Sign-On via SAM v2.0:
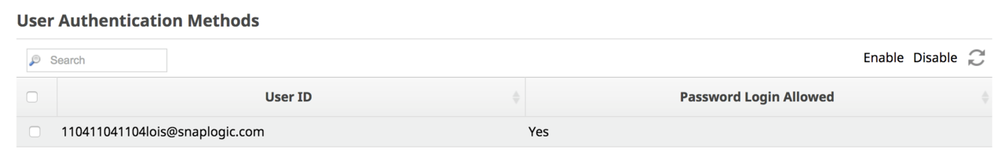
The User Authentication Methods page opens.
...
- Select the appropriate user IDs and click
...
- Disable
...
- .
...
| Info |
|---|
The Manager Password Logins button does not show in Classic Manager settings until you configure SSO. |
Multi-Factor Authentication
To add multi-factor authentication (MFA) when using SSO:
- Configure your IdP to require MFA. Consult the IdP documentation for more information.
- If password login is not disabled for all SnapLogic user accounts, edit multiple accounts as described in the Manage Password Logins section above.
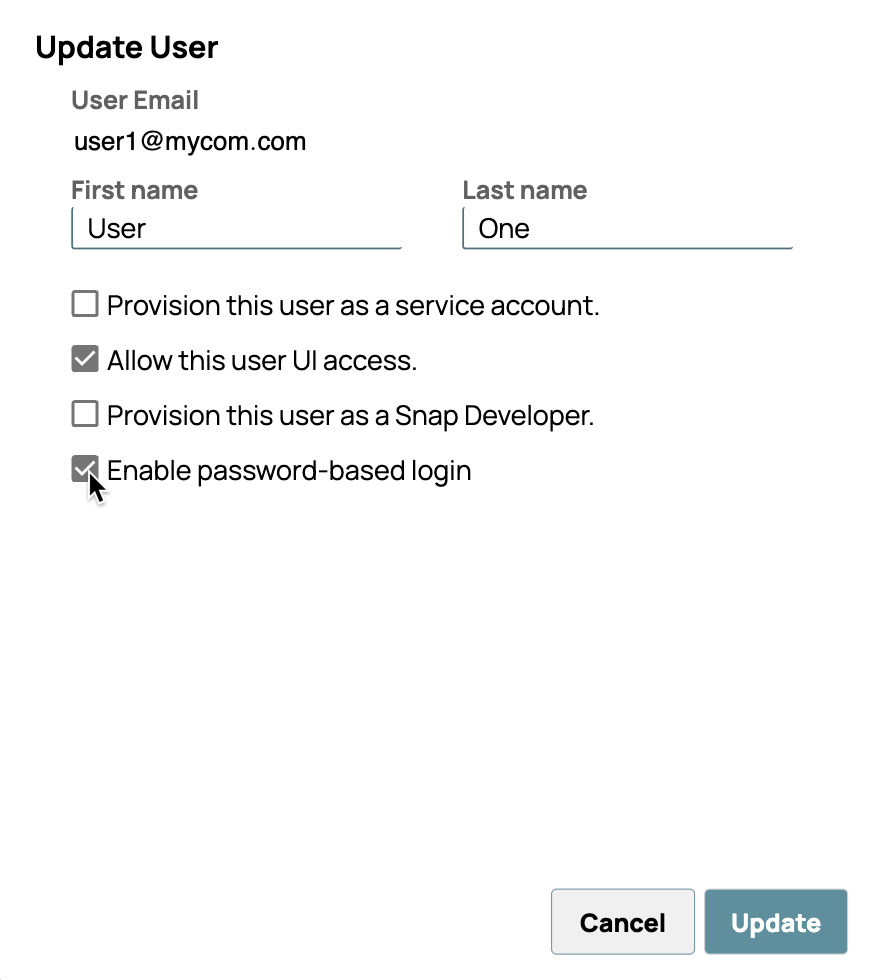
To edit a single account, you can alternatively:- In Classic Manager, from the left navigation pane, select Users.
- Click a user account to select it.
- Click Edit.
- Click to de-select Enable password-based login:
- Click Update.
...
Related Content
- Two-way SSL with SnapLogic’s REST Snap
- Configuring Azure Active Directory SSO Configuration with SnapLogic
...