SQS Account
In this article
Overview
You can use this account type to connect Amazon SQS Snaps with data sources that use SQS accounts.
Prerequisites
The permission policies, set up by the account administrator, govern all the SQS resources. These policies can either be identity-based or are set up separately for SQS. Ensure that your SQS account has the appropriate permission policy when setting it up in SnapLogic. Specifically, you need sqs:ListQueues permission to validate the SQS account in SnapLogic. For more information, see Access Management Overview.
Limitations
None.
Behavior Change
With the 432patches19990, the Amazon SQS account reauthenticates when the authentication expires; the account automatically retires authentication on encountering 401 or 403 errors.
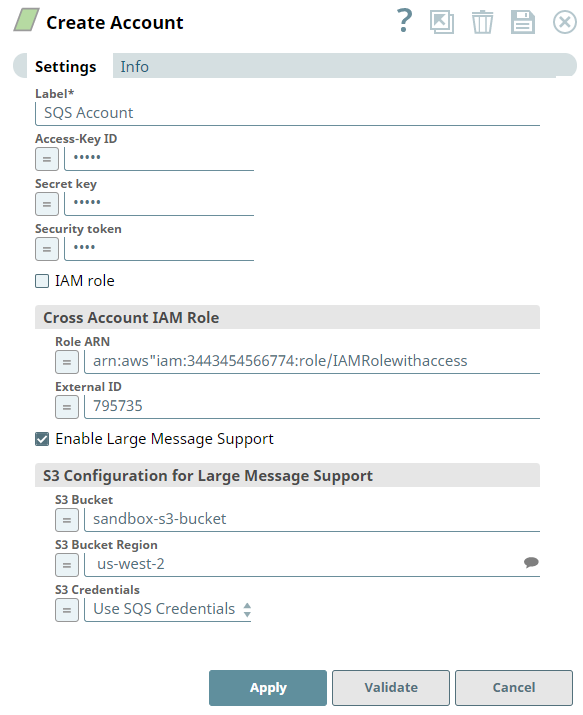
Account Settings
Field Name | Field Dependency | Description |
|---|---|---|
Label* | N/A | Specify a unique label for the account. Default Value: N/A |
Access-key Id | N/A | Specify the access key ID of AWS authentication. Default value: N/A |
| Secret key | N/A | Specify the secret key of AWS authentication. Default value: N/A |
| Security token | N/A | Specify a security token that is part of AWS Security Token Service (STS) credentials. Note that only global Security Token Service (STS) regions are supported. Default value: N/A Example: z7PmG8F6DY5xblJHwN |
| IAM role | N/A | Select this checkbox to enable the IAM role stored in the EC2 instance to access SQS. Access-key ID and Secret key are ignored. This feature is valid only in EC2-type Groundplex. Refer to the Snap reference document for the required entry in the global properties file. Default value: Not selected |
Cross Account IAM Role | Use this field set to set up cross-account IAM role access. It consists of the following fields:
| |
Role ARN | N/A | Specify the Amazon Resource Name of the role to assume. Default value: None |
External ID | N/A | Specify an optional external ID that might be required by the role to assume. Default value: None |
| Enable Large Message Support | N/A | Select this checkbox to enable the Snap to send and receive large messages with size more than 256KB. The AWS extended library uses S3 only if the message size is more than 256 KB. However, you cannot enable the Client-side buffering option in Amazon SQS Snaps if you select the Enable Large Message Support checkbox in your SQS account. |
| S3 Configuration | If Enable Large Message Support checkbox is selected. | Use this field set to configure the S3 bucket details. It consists of the following fields:
|
| S3 Bucket | If Enable Large Message Support checkbox is selected. | Specify the S3 Bucket name residing in an external AWS account. If the field is lefty empty, the default region (the region of the EC2 instance, or us-west-2 if the JCC is not on a EC2) will be used. Default value: None |
| S3 Bucket Region | If Enable Large Message Support checkbox is selected. | Specify the region where the S3 Bucket is residing. Default value: None |
| S3 Credentials | If Enable Large Message Support checkbox is selected. | Choose the S3 credentials for the S3 bucket. The available options are:
Default value: Use SQS Credentials |
| S3 Acess Key ID | If Provide Separate Credentials is selected for S3 Credentials. | Specify the S3 access key ID that you want to use for AWS authentication. |
| S3 Secret Key | If Provide Separate Credentials is selected for S3 Credentials. | Specify the S3 secret key associated with the S3 Access-ID key listed in the S3 Access-key ID field. |
| Use EC2 Role | If Provide Separate Credentials is selected for S3 Credentials. | Select this checkbox to use Amazon Elastic Cloud Compute Role. |
| Assumed Role ARN | If Provide Separate Credentials is selected for S3 Credentials. | Specify the Amazon Resource Name of the role to assume. |
| Assumed Role External ID | If Provide Separate Credentials is selected for S3 Credentials. | Specify an optional external ID that might be required by the role to assume. |
Troubleshooting
| Error | Reason | Resolution |
|---|---|---|
| Invalid account configuration. | You might have entered empty or null values in Cross Account IAM Role fields. | Enter valid values for Cross Account IAM Role. |
MISSING_GROUP_ID | Message group ID is missing. | Message group ID is mandatory for FIFO Queue. Enter a valid Message group ID. |
| BUFFER_NOT_SUPPORT_FIFO | Client-side buffering cannot be enabled for FIFO Queue. | Deselect client-side buffering or use standard queue. |
| VALIDATE_ACCOUNT_WITH_EXPRESSION | One or more Pipeline parameters must be configured in the Pipeline. Validation is not applicable for Pipeline parameters. | Do not validate the account if you provide Pipeline parameters. |
| ACCOUNT_CREDENTIALS_MISSING | Either Access key and secret key might be empty. | You must provide valid credentials for SQS if the IAM role is disabled. |
See Also
Have feedback? Email documentation@snaplogic.com | Ask a question in the SnapLogic Community
© 2017-2025 SnapLogic, Inc.