Configuring MongoDB Accounts
Kalpana Malladi
Aparna Tayi (Unlicensed)
Gouri Bhagchandani (Deactivated)
On this Page
This account is used by the Snaps in the MongoDB Snap Pack.
Account Configuration
In SnapLogic, you can create accounts either for projects or in shared folders.
To create a MongoDB account:
- Click on the project or shared folder for which you want to create the account. This displays a page that displays all the resources associated with the project or folder.
- Click Create > MongoDB, and then choose the MongoDB Account you want to create.
- Select MongoDB Account to connect to a single node.
Select Replica Set Account to connect to replica sets for operations. For more information on replication in MongoDB, see the Replication page in MongoDB documentation.
To add an account for MongoDB Atlas, you must configure an account as either Replica Set or Replica Set Dynamic Account because MongoDB Atlas starts with a replica set of 3 nodes. Read more on connecting MongoDB Atlas via drivers.
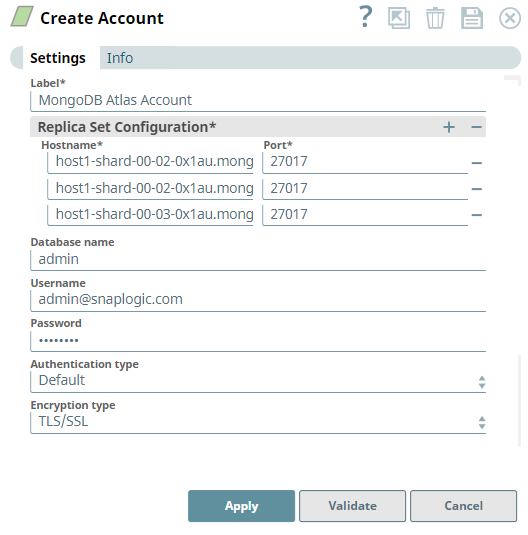
- Supply a Label for the account.
- Supply the necessary information for the appropriate account type:
- MongoDB Account
- Replica Set Account
- MongoDB Dynamic Account
- Replica Set Dynamic Account
For detailed guidance on setting up each of these accounts, see the Account Types section below.
- Supply additional information on this account in the Notes field of the Info tab.
Account Types
MongoDB Account
Label | Required. User provided label for the account instance. Default value: [None] | |
|---|---|---|
Hostname | Required. MongoDB Hostname Default value: [None] | |
Port | Required. The MongoDB Port. Default value: [None] | |
Database name | The database that the MongoDB account is defined in. This is also the default database used for queries. Ensure to provide the database name when selecting the TLS/SSL option in the Encryption type property. Default value: [None] | |
Username | Required. The MongoDB Username. Default value: [None] | |
Password | Required. The password associated with the MongoDB Username. Default value: [None] | |
Authentication type | Required. The authentication type that you want to use with this account. The options available are:
| |
Encryption type | Required. The encryption type for connecting Mongo instance. The options available are None, TLS/SSL and SSL certs If None is selected, data is not encrypted. If TLS/SSL is selected, data is encrypted without certificate validation. Ensure to provide the database name in the Database name property to validate the user against that particular database name. If SSL certs is Selected, the data is encrypted ensuring the certificate validation. Default value: None | |
| SSL certs properties | Conditional. Configure the keystore and truststore properties only when the encryption type is selected as "SSL certs". This ensures the validation of the certificate. | |
| Truststore filepath | The location of the trust store file in PKCS#12 format, can be in SLDB or any other unauthenticated endpoint such as https://... Example: shared/cacert_keystore.p12 | |
| Truststore password | Truststorepassword to access the truststore file of the server. | |
| Keystore filepath | The location of the key store file in PKCS#12 format, can be in SLDB or any other unauthenticated endpoint such as https://... Example: shared/client_keystore.p12 | |
| Keystore file password | Keystore password to access the keystore file of the client. | |
| Connection properties | Configure the connection properties to specify connection and server selection timeouts. | |
| Connection timeout (seconds) | The number of seconds the Mongo driver waits before aborting a new connection attempt. A value of 0 seconds specifies an infinite timeout. Default value: 10 | |
| Server Selection timeout (seconds) | The number of seconds the Mongo driver waits to select a server for an operation before aborting the selection. For example, if you set the Server Selection timeout to 30 seconds, and the Snap fails to find a server until 30 seconds, the pipeline logs an error and aborts execution. A value of 0 seconds specifies an infinite timeout. Default value: 30 | |
| MongoDB cursor properties | Use this field set to configure the MongoDB cursor timeout properties. | |
| Use Cursor Timeout | Select this checkbox to set a timeout for idle cursors, which means, it enables the server to close a cursor automatically after a period of inactivity. This option allows you to connect to Atlas Free Tier database and Shared Clusters using the MongoDB accounts. Refer to Atlas Free Tier limitations for more information. For all the existing Mongo DB accounts, the Use Cursor Timeout check box is deselected by default. Default value: Not Selected | |
Account Encryption
| Standard Encryption | If you are using Standard Encryption, the High sensitivity settings under Enhanced Encryption are followed. | |
|---|---|---|
| Enhanced Encryption | If you have the Enhanced Account Encryption feature, the following describes which fields are encrypted for each sensitivity level selected for this account. Account:
| |
Replica Set Account
Label | Required. User provided label for the account instance. Default value: [None] | ||
|---|---|---|---|
Replica Set Configuration | Required. Hostnames and ports for MongoDB replica set. Default value: [None] | ||
Hostname | The MongoDB Hostname | ||
Port | The MongoDB port. Default value: [None] | ||
Database name | Required. The database that the MongoDB account is defined in. This is also the default database used for queries. Default value: None To validate a MongoDB Atlas account, enter the name as admin. Alternatively, to override the actual database name in the Database name property at the Snap settings level. | ||
Username | Required. MongoDB Username Default value: [None] | ||
Password | Required. The password associated with the MongoDB Username. Default value: [None] | ||
Authentication type | Required. The authentication type that you want to use with this account. The options available are:
Default value: Default | ||
Encryption type | Required. The encryption type for connecting Mongo instance. The options available are None, TLS/SSL and SSL certs If None is selected, data is not encrypted. If TLS/SSL is selected, data is encrypted without certificate validation. If SSL certs is Selected, the data is encrypted ensuring the certificate validation. Default value: None To validate a MongoDB Atlas account, select TLS/SSL. | ||
| SSL certs properties | Conditional. Configure the keystore and truststore properties only when the encryption type is selected as "SSL certs". This ensures the validation of the certificate. | ||
| Truststore filepath | The location of the trust store file in PKCS#12 format, can be in SLDB or any other unauthenticated endpoint such as https://... Example: shared/cacert_keystore.p12 | ||
| Truststore password | Truststorepassword to access the truststore file of the server. | ||
| Keystore filepath | The location of the key store file in PKCS#12 format, can be in SLDB or any other unauthenticated endpoint such as https://... Example: shared/client_keystore.p12 | ||
| Keystore file password | Keystore password to access the keystore file of the client. | ||
| Connection properties | Configure the connection properties to specify connection and server selection timeouts. | ||
| Connection timeout (seconds) | The number of seconds the Mongo driver waits before aborting a new connection attempt. A value of 0 seconds specifies an infinite timeout. Default value: 10 | ||
| Server Selection timeout (seconds) | The number of seconds the Mongo driver waits to select a server for an operation before aborting the selection. For example, if you set the Server Selection timeout to 30 seconds, and the Snap fails to find a server until 30 seconds, the pipeline logs an error and aborts execution. A value of 0 seconds specifies an infinite timeout. Default value: 30 | ||
| MongoDB cursor properties | Use this field set to configure the MongoDB cursor timeout properties. | ||
| Use cursor timeout | Select this checkbox to set a timeout for idle cursors, which means, it enables the server to close a cursor automatically after a period of inactivity. This option allows you to connect to Atlas Free Tier database and Shared Clusters using the MongoDB accounts. Refer to Atlas Free Tier limitations for more information. For all the existing Mongo DB accounts, the Use Cursor Timeout check box is deselected by default. Default value: Not Selected | ||
Read preference |
| ||
Account Encryption
| Standard Encryption | If you are using Standard Encryption, the High sensitivity settings under Enhanced Encryption are followed. | |
|---|---|---|
| Enhanced Encryption | If you have the Enhanced Account Encryption feature, the following describes which fields are encrypted for each sensitivity level selected for this account. Account:
| |
MongoDB Dynamic Account
Label | Required. User provided label for the account instance. Default value: [None] | |
|---|---|---|
Hostname | Required. The MongoDB Hostname. Enable the expression property to use a pipeline parameter. Default value: [None] | |
Port | Required. The MongoDB port. Enable the expression property to use a pipeline parameter. Default value: [None] | |
Database name | Required. The database that the MongoDB account is defined in. This is also the default database used for queries. Enable the expression property to use a pipeline parameter. Example: _dbName Default value: [None] | |
Username | Required. MongoDB Username Enable the expression property to use a pipeline parameter. Default value: [None] | |
Password | Required. The password associated with the MongoDB Username Enable the expression property to use a pipeline parameter. Default value: [None] | |
Authentication type | Required. The authentication type that you want to use with this account. The options available are:
Default value: Default | |
Encryption type | Required. The encryption type for connecting Mongo instance. The options available are None, TLS/SSL and SSL certs If None is selected, data is not encrypted. If TLS/SSL is selected, data is encrypted without certificate validation. If SSL certs is Selected, the data is encrypted ensuring the certificate validation. Default value: None | |
| SSL certs properties | Conditional. Configure the keystore and truststore properties only when the encryption type is selected as "SSL certs". This ensures the validation of the certificate. | |
| Truststore filepath | The location of the trust store file in PKCS#12 format, can be in SLDB or any other unauthenticated endpoint such as https://... Example: shared/cacert_keystore.p12 | |
| Truststore password | Truststorepassword to access the truststore file of the server. | |
| Keystore filepath | The location of the key store file in PKCS#12 format, can be in SLDB or any other unauthenticated endpoint such as https://... Example: shared/client_keystore.p12 | |
| Keystore file password | Keystore password to access the keystore file of the client. | |
| Connection properties | Configure the connection properties to specify connection and server selection timeouts. | |
| Connection timeout (seconds) | The number of seconds the Mongo driver waits before aborting a new connection attempt. A value of 0 seconds specifies an infinite timeout. Default value: 10 | |
| Server Selection timeout (seconds) | The number of seconds the Mongo driver waits to select a server for an operation before aborting the selection. For example, if you set the Server Selection timeout to 30 seconds, and the Snap fails to find a server until 30 seconds, the pipeline logs an error and aborts execution. A value of 0 seconds specifies an infinite timeout. Default value: 30 | |
| MongoDB cursor properties | Use this field set to configure the MongoDB cursor timeout properties. | |
| Use cursor timeout | Select this checkbox to set a timeout for idle cursors, which means, it enables the server to close a cursor automatically after a period of inactivity. This option allows you to connect to Atlas Free Tier database and Shared Clusters using the MongoDB accounts. Refer to Atlas Free Tier limitations for more information. For all the existing Mongo DB accounts, the Use Cursor Timeout check box is deselected by default. Default value: Not Selected | |
Account Encryption
| Standard Encryption | If you are using Standard Encryption, the High sensitivity settings under Enhanced Encryption are followed. | |
|---|---|---|
| Enhanced Encryption | If you have the Enhanced Account Encryption feature, the following describes which fields are encrypted for each sensitivity level selected per each account. Account:
| |
Example
Setting a MongoDB Dynamic Account
Selecting the Dynamic Account allows the users to pass the account details dynamically as a pipeline parameter. This would enable the users to use the same Snap within a pipeline to connect to different database instances.
For the pipeline, define the pipeline parameters:
- hostname
- database
- username
- password
- port
You will supply values for them in the Dynamic Account.
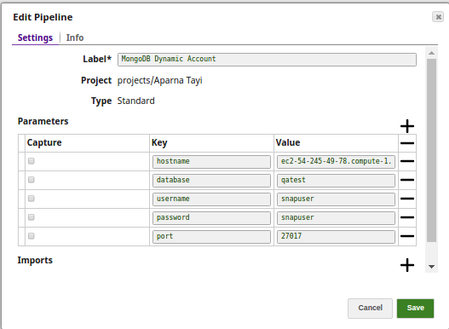
In DynamoDB - Update pipeline, create a DynamoDB Dynamic Account (In this pipeline the MongoDB Update Snap is updating the documents on a MongoDB collection in a JSON format using the JSON Generator Snap).
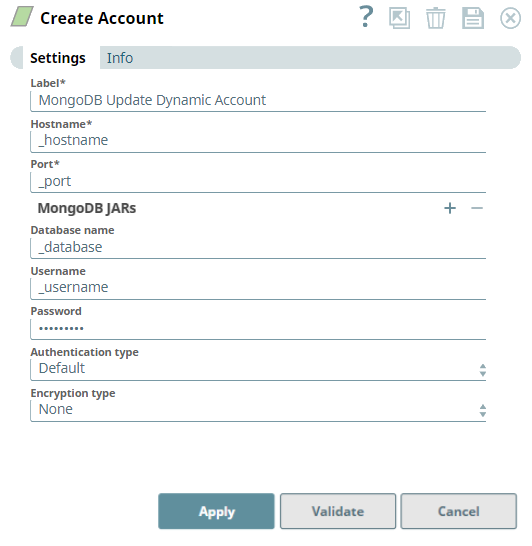
- Set the expression toggle on for the properties you want to pass the values dynamically.
Set Hostname to _hostname, Port to _port, Database Name to _database, Username to _username, and Password to _password.
- Click Apply and fill the Snap Settings for the desired function.
Replica Set Dynamic Account
Label | User provided label for the account instance | ||
|---|---|---|---|
Replica Set Configuration | Hostnames and ports for MongoDB replica set. Default value: [None] | ||
Hostname | The MongoDB Hostname. Default value: [None] | ||
Port | The MongoDB port. Default value: [None] | ||
Database name | The database that the MongoDB account is defined in. This is also the default database used for queries. Enable the expression property to use a pipeline parameter. Example: _dbName Default value: None To validate a MongoDB Atlas account, enter the name as admin. Alternatively, to override the actual database name in the Database name property at the Snap settings level. | ||
Username | The MongoDB Username. Enable the expression property to use a pipeline parameter. Example: _username Default value: [None] | ||
| Password | The password associated with the MongoDB Username. Example: _password Default value: [None] | ||
| Authentication type | Required. The authentication type that you want to use with this account. The options available are:
Default value: Default | ||
Encryption type | Required. The encryption type for connecting Mongo instance. The options available are None, TLS/SSL and SSL certs If None is selected, data is not encrypted. If TLS/SSL is selected, data is encrypted without certificate validation. If SSL certs is Selected, the data is encrypted ensuring the certificate validation. Default value: None To validate a MongoDB Atlas account, select TLS/SSL. | ||
| SSL certs properties | Conditional. Configure the keystore and truststore properties only when the encryption type is selected as "SSL certs". This ensures the validation of the certificate. | ||
| Truststore filepath | The location of the trust store file in PKCS#12 format, can be in SLDB or any other unauthenticated endpoint such as https://... Example: shared/cacert_keystore.p12 | ||
| Truststore password | Truststorepassword to access the truststore file of the server. | ||
| Keystore filepath | The location of the key store file in PKCS#12 format, can be in SLDB or any other unauthenticated endpoint such as https://... Example: shared/client_keystore.p12 | ||
| Keystore file password | Keystore password to access the keystore file of the client. | ||
| Connection properties | Configure the connection properties to specify connection and server selection timeouts. | ||
| Connection timeout (seconds) | The number of seconds the Mongo driver waits before aborting a new connection attempt. A value of 0 seconds specifies an infinite timeout. Default value: 10 | ||
| Server Selection timeout (seconds) | The number of seconds the Mongo driver waits to select a server for an operation before aborting the selection. For example, if you set the Server Selection timeout to 30 seconds, and the Snap fails to find a server until 30 seconds, the pipeline logs an error and aborts execution. A value of 0 seconds specifies an infinite timeout. Default value: 30 | ||
| MongoDB cursor properties | Use this field set to configure the MongoDB cursor timeout properties. | ||
| Use cursor timeout | Select this checkbox to set a timeout for idle cursors, which means, it enables the server to close a cursor automatically after a period of inactivity. This option allows you to connect to Atlas Free Tier database and Shared Clusters using the MongoDB accounts. Refer to Atlas Free Tier limitations for more information. For all the existing Mongo DB accounts, the Use Cursor Timeout check box is deselected by default. Default value: Not Selected | ||
Read preference |
| ||
Account Encryption
| Standard Encryption | If you are using Standard Encryption, the High sensitivity settings under Enhanced Encryption are followed. | |
|---|---|---|
| Enhanced Encryption | If you have the Enhanced Account Encryption feature, the following describes which fields are encrypted for each sensitivity level selected per each account. Account:
| |
Snap Pack History
| Release | Snap Pack Version | Date | Type | Updates |
|---|---|---|---|---|
| February 2025 | 440patches29949 | Latest | Upgraded the Spring Framework version to 5.3.39. | |
| February 2025 | main29887 | Stable | Updated and certified against the current SnapLogic Platform release. | |
| November 2024 | main29029 | Stable | Enhanced the MongoDB Replica and Mongo ReplicaSet Dynamic Accounts to define read preference options when querying data. The default option is Primary, so you cannot allocate read load to the secondary node. Note that the Secondary preferred mode is not supported for the MongoDB Execute Snap. | |
August 2024 | main27765 | | Stable | Updated and certified against the current SnapLogic Platform release. |
| May 2024 | 437patches27343 | Latest | The MongoDB - Atlas Vector Search Snap now supports the following:
| |
| May 2024 | 437patches26832 | Latest |
| |
| May 2024 | 437patches26721 | Latest |
| |
| May 2024 | main26341 | Stable |
| |
| February 2024 | 436patches26244 | Latest | Added the following Snap to the MongoDB Snap Pack:
| |
| February 2024 | 436patches25893 | Latest | Added MongoDB Execute Snap to the MongoDB Snap Pack. | |
| February 2024 | main25112 | Stable | Updated and certified against the current SnapLogic Platform release. | |
| November 2023 | main23721 | Stable | Updated and certified against the current SnapLogic Platform release. | |
August 2023 | main22460 | | Stable | Updated and certified against the current SnapLogic Platform release. |
May 2023 | main21015 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| February 2023 | main19844 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| November 2022 | main18944 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| September 2022 | 430patches18223 | Latest | The MongoDB Update Snap in a low-latency feed Ultra Pipeline now correctly acknowledges the requests. | |
| August 2022 | 430patches17472 | Latest | The MongoDB Account with Encryption type set to TLS/SSL does not fail with the "URL cannot be null" error. | |
| August 2022 | main17386 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.29Patches | 429patches15807 | Latest | Updated the expected output for the MongoDB - Update Snap that is changed because of the upgrade of Spring Core framework version. | |
4.29 | main15993 |
| Stable | Upgraded with the latest SnapLogic Platform release. |
| 4.28 | main14627 | Stable | Upgraded with the latest SnapLogic Platform release. | |
4.27 | main12833 | | Stable | Upgraded with the latest SnapLogic Platform release. |
| 4.26 | main11181 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.25 | main9554 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.24 | main8556 | Stable | Fixed an issue in the MongoDB accounts to connect to Atlas Free Tier and Shared Cluster database using the Use cursor timeout checkbox in the MongoDB cursor properties. If selected, this option enables the server to close a cursor automatically after a period of inactivity. For the existing accounts that does not have this field, the value for this checkbox returns false, which is backward compatible. | |
| 4.23 | main7430 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.22 | main6403 | Stable | Upgraded with the latest SnapLogic Platform release. | |
4.21 Patch | 421patches6272 | Latest | Fixes the issue where Snowflake SCD2 Snap generates two output documents despite no changes to Cause-historization fields with DATE, TIME and TIMESTAMP Snowflake data types, and with Ignore unchanged rows field selected. | |
4.21 Patch | 421patches6144 | Latest | Fixes the following issues with DB Snaps:
| |
| 4.21 Patch | MULTIPLE8841 | Latest | Fixes the connection issue in Database Snaps by detecting and closing open connections after the Snap execution ends. | |
| 4.21 | snapsmrc542 |
| Stable | Upgraded with the latest SnapLogic Platform release. |
| 4.20 | snapsmrc535 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.19 | snaprsmrc528 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.18 | snapsmrc523 | Stable |
| |
| 4.17 | ALL7402 | Latest | Pushed automatic rebuild of the latest version of each Snap Pack to SnapLogic UAT and Elastic servers. | |
| 4.17 Patch | db/mongo7331 | Latest |
| |
| 4.17 | snapsmrc515 | Latest | Added the Snap Execution field to all Standard-mode Snaps. In some Snaps, this field replaces the existing Execute during preview check box. | |
| 4.16 | snapsmrc508 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.15 Patch | db/mongo6783 | Latest | Fixed connection timeout issue with MongoDB. | |
| 4.15 Patch | db/mongo6465 | Latest | Fixed an issue wherein REST calls to Ultra tasks returned an error message. | |
| 4.15 | snapsmrc500 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.14 Patch | db/mongo5666 | Latest | Fixed the Update, Delete, and Find Snaps to populate input view schema for a given table, similar to the Insert Snap. | |
| 4.14 | snapsmrc490 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.13 Patch | mongo5537 | Latest | Fixed the Update, Delete, and Find Snaps to populate input view schema for a given table, similar to the Insert Snap. | |
| 4.13 | snapsmrc486 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.12 | snapsmrc480 | Stable | Added the SSl certification properties to all the MongoDB Accounts to ensure the validation of the certificate. | |
| 4.11 | snapsmrc465 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.10 Patch | mongo3978 | Latest | Resolved an issue where the NumberFormatException was not handled properly for some of the valid Number Types like "NaN"/ "+Infinity"/ "-Infinity". | |
| 4.10 | snapsmrc414 | Stable | Upgraded with the latest SnapLogic Platform release. | |
| 4.9.0 Patch | mongodb3259 | Latest |
| |
| 4.9 | snapsmrc405 | Stable |
| |
| 4.8.0 Patch | mongodb2735 | Latest | Added SSL encryption type to all MongoDB accounts and Replica set Accounts and removed the MongoDB SSL account. | |
| 4.8 | snapsmrc398 | Stable |
| |
| 4.7 Patch | mongo2375 | Latest |
| |
| 4.7 Patch | mongo2338 | Latest | Add an account for MongoDB SSL connection without certificates validation | |
| 4.7 Patch | mongo2200 | Latest | Fixed an issue for database Select Snaps regarding Limit rows not supporting an empty string from a pipeline parameter. | |
| 4.7 | snapsmrc382 | Stable | Updated the Snap account with the LDAP Authentication type. | |
| 4.6 | snapsmrc362 | Stable | Resolved an issue in MongoDB Insert Snap that processed and inserted all numeric fields as strings. | |
| 4.5.1 | snapsmrc344 | Stable |
| |
| 4.3.2 | Stable | Resolved an issue with MongoDB Find returning nothing when nothing was found. | ||
| 4.3 | Stable |
| ||
| 4.2.2 | Stable |
| ||
| 4.2.1 | Stable |
|
Have feedback? Email documentation@snaplogic.com | Ask a question in the SnapLogic Community
© 2017-2025 SnapLogic, Inc.