Configuring Redshift Accounts
In this article
Overview
You must create SnapLogic Redshift Accounts to connect to data sources that you want to use in your pipelines. You can configure your SnapLogic Redshift Accounts using either the Designer or the Manager.
Redshift IAM Account Setup This applies only to the Redshift - Bulk Load, Redshift - Unload, and Redshift - S3 Upsert Snaps.
If you use the PostgreSQL driver (org.postgresql.Driver) with the Redshift Snap Pack, it could result in errors if the data type provided to the Snap does not match the data type in the Redshift table schema. Either use the Redshift driver (com.amazon.redshift.jdbc42.Driver) or use the correct data type in the input document to resolve these errors.
Snap-Account Compatibility
Snaps in the Redshift Snap Pack work with different accounts and protocols per the following table.
| Snap | ||||
|---|---|---|---|---|
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ | |
| ✔ | ✔ | ✔ | ✔ |
Configuring Redshift Accounts Using SnapLogic Designer
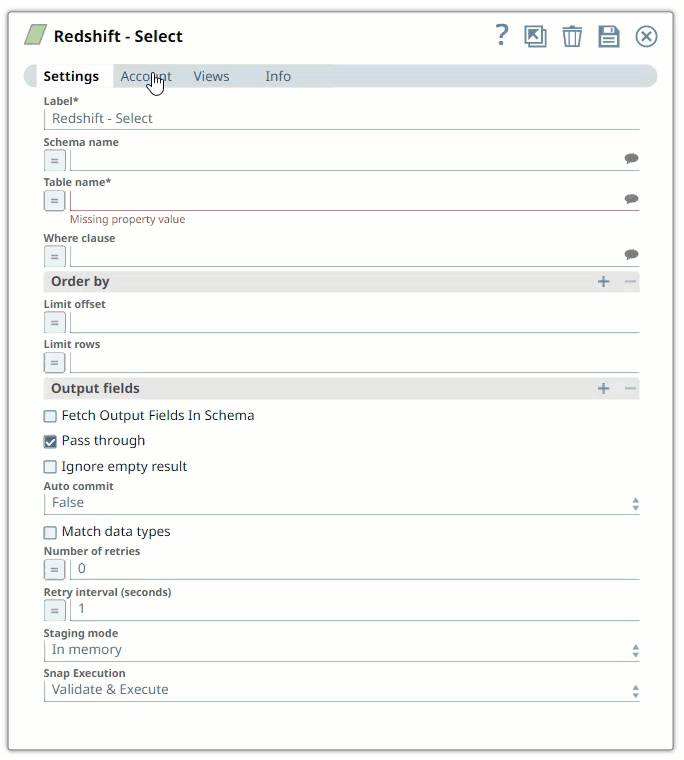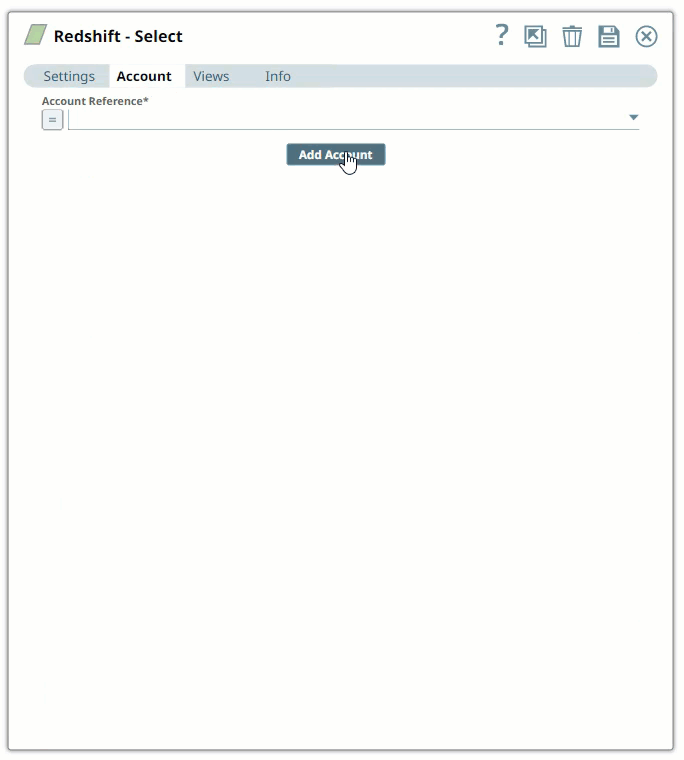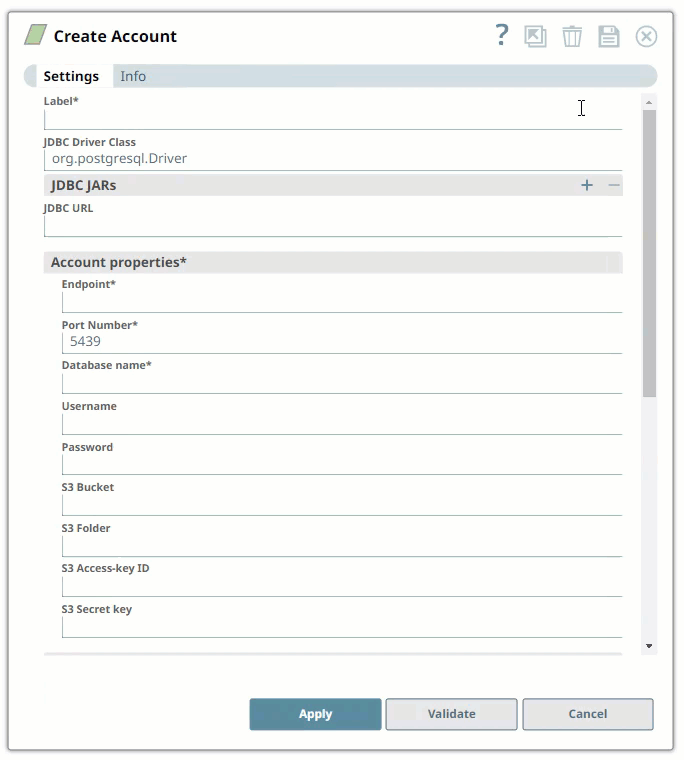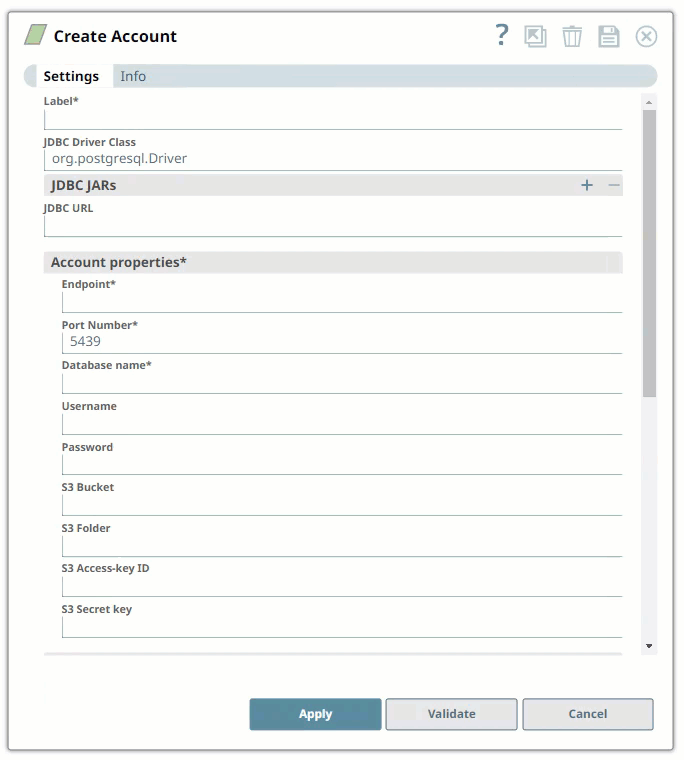
Drag a Redshift Snap to the Canvas and click the Snap to open its settings. Click the Account tab. You can now either use an existing account or create a new one.
Selecting an existing account
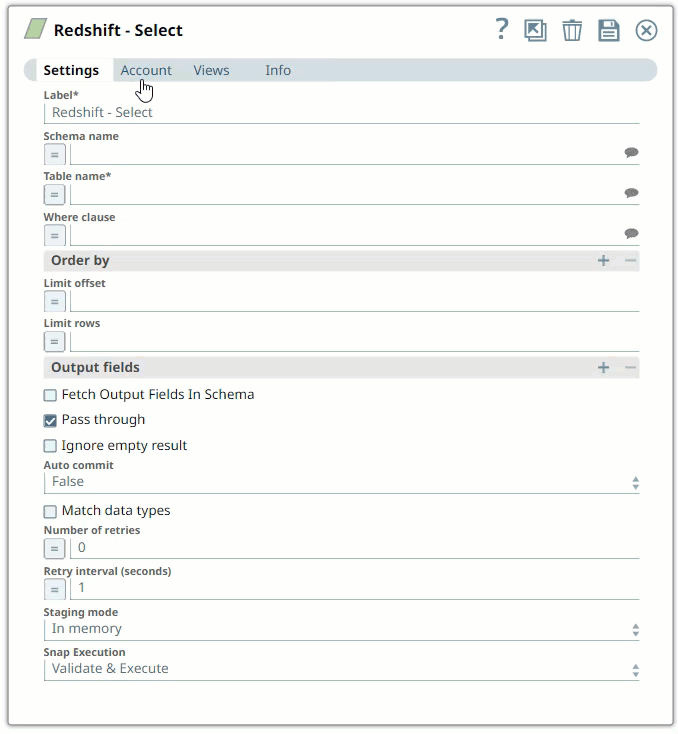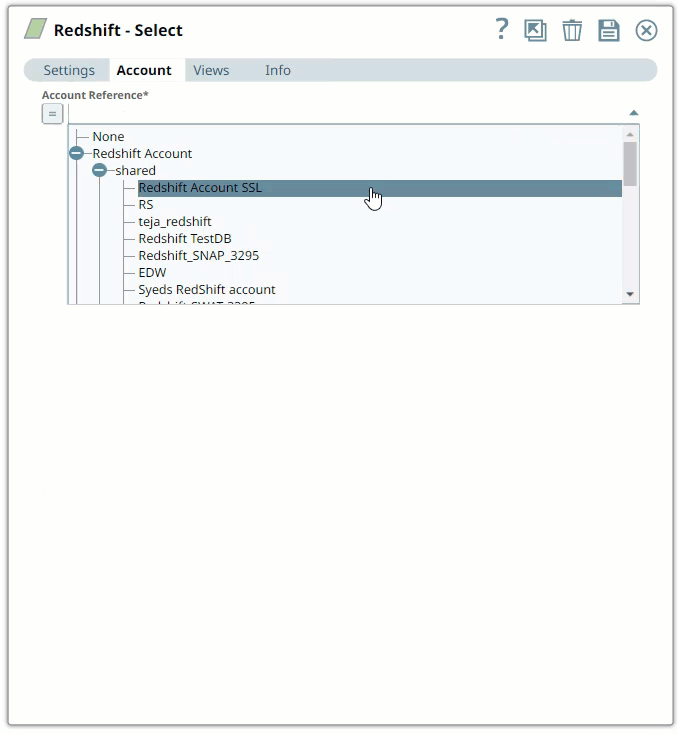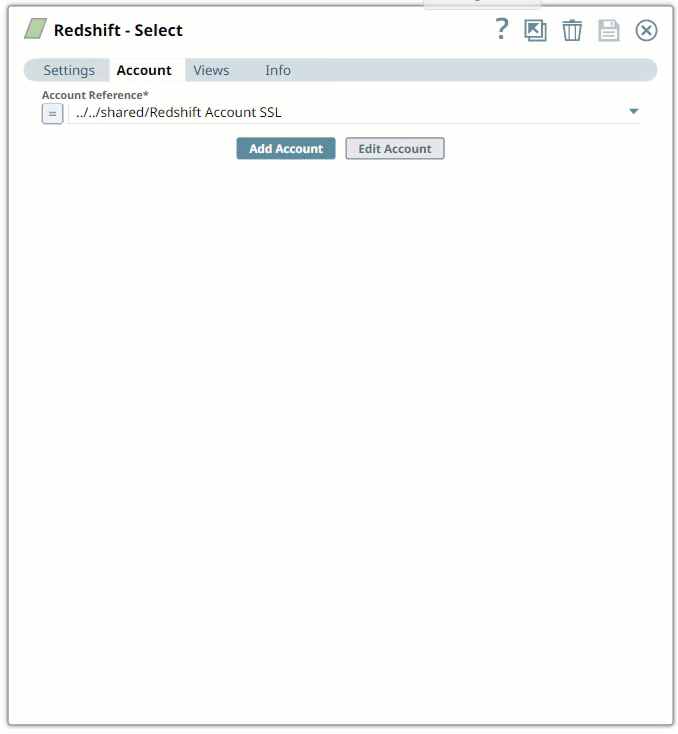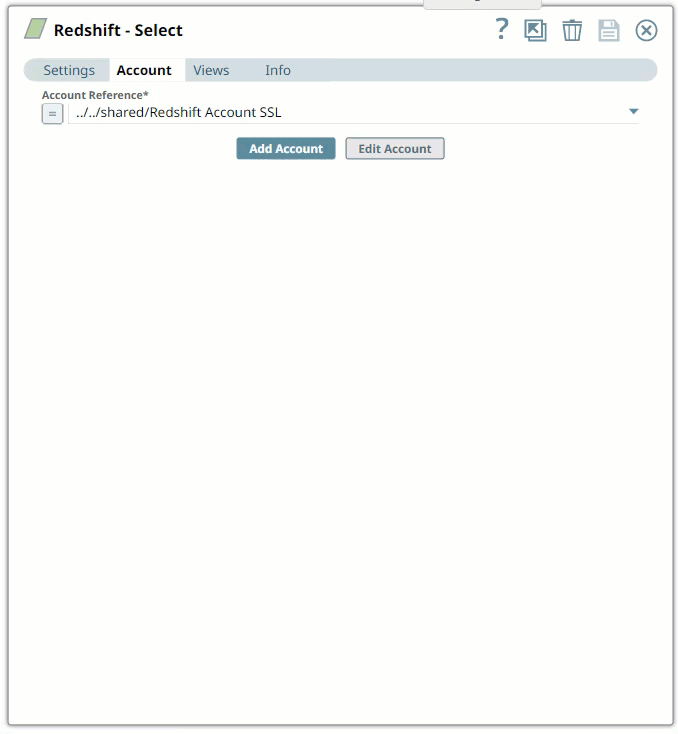
SnapLogic organizes and displays all accounts to which you have access, sorting them by account type and location. To select an existing account:
In the Account tab, click the icon to view the accounts to which you have access, and select the account that you want to use.
Click Save.
Creating an account
In the Account tab, click Add Account below the Account Reference field.
Select the Location in which you want to create the account, select the Account Type, and click Continue. The Add Account dialog window associated with the account type is displayed.
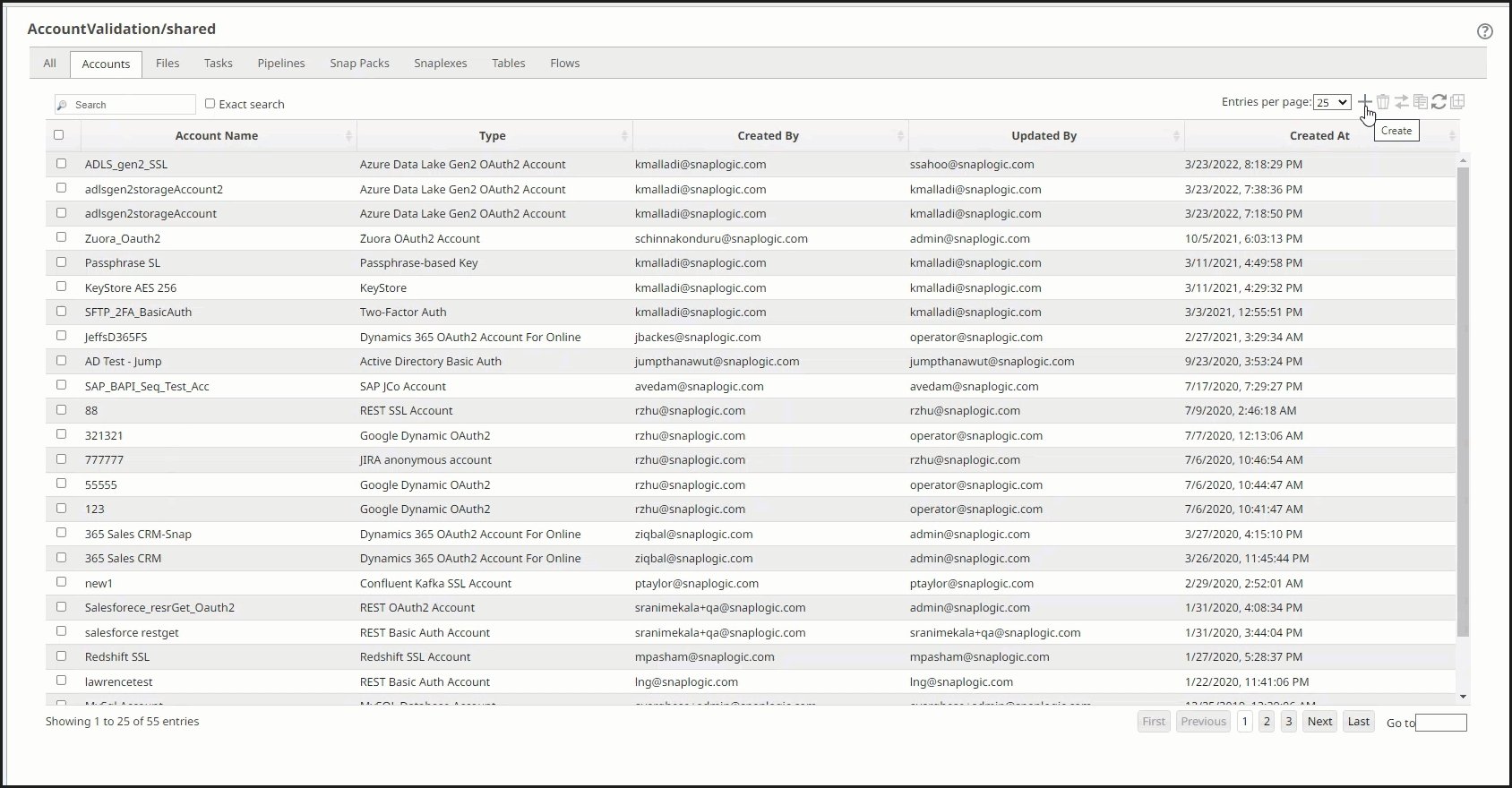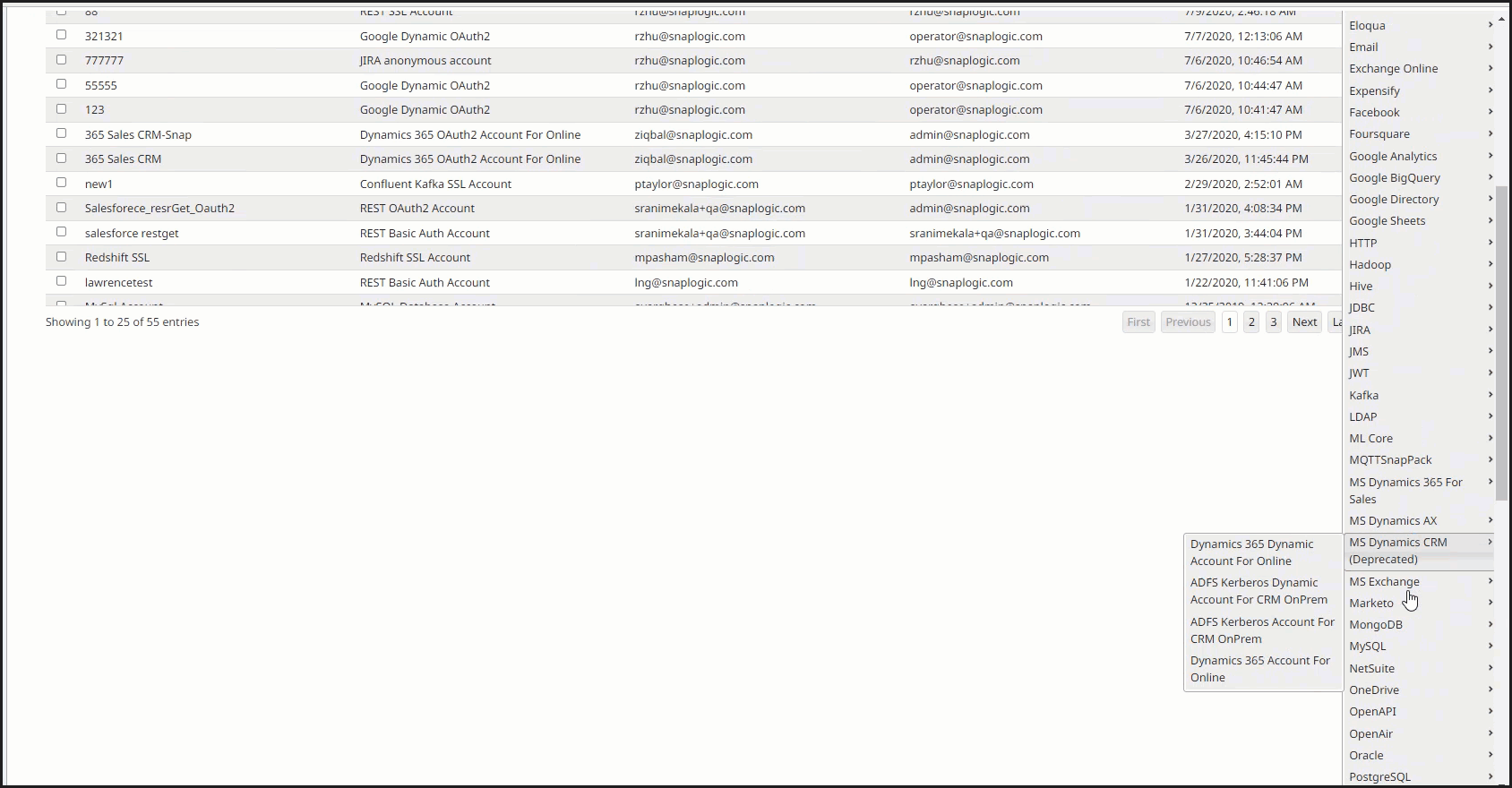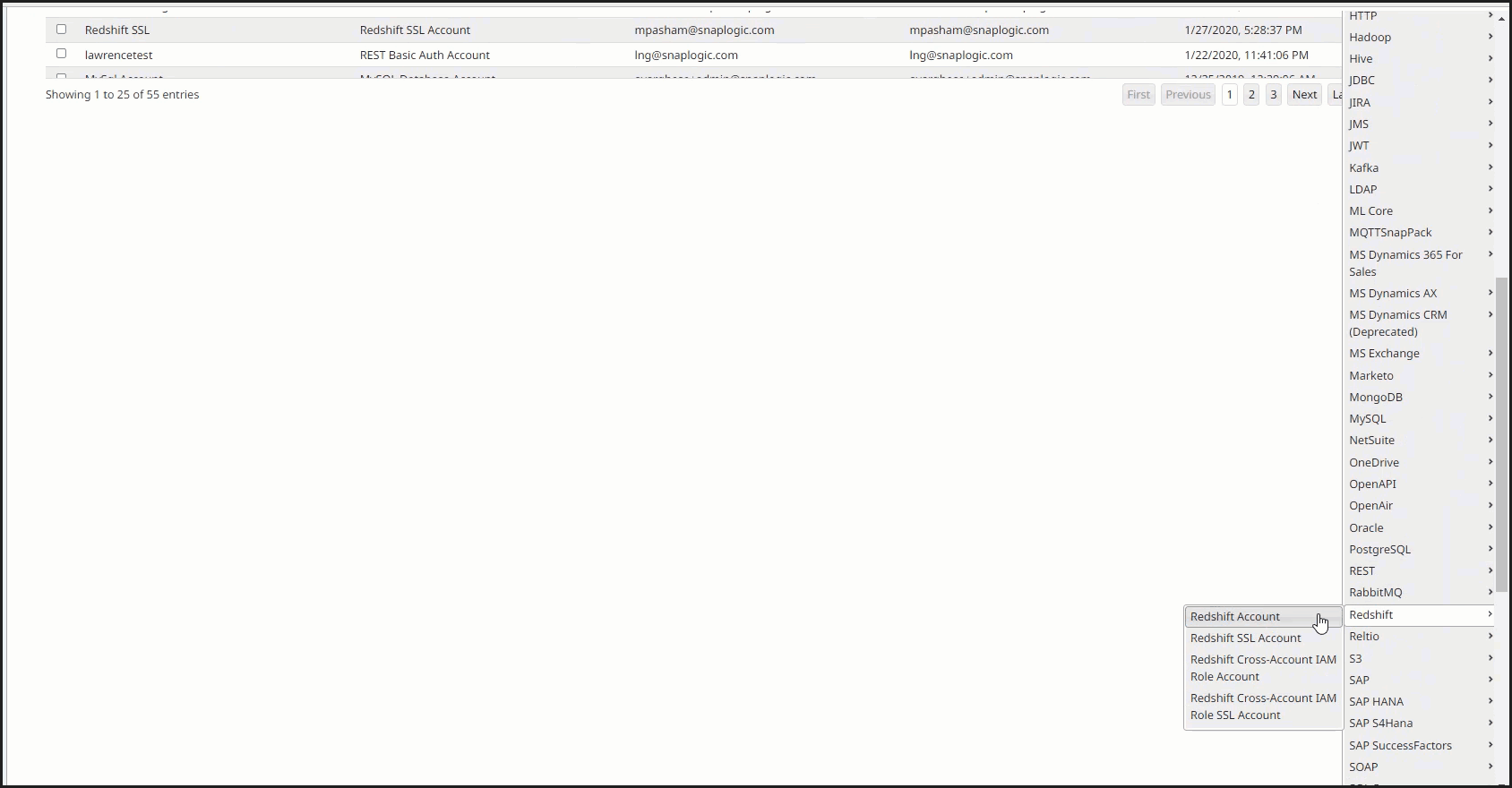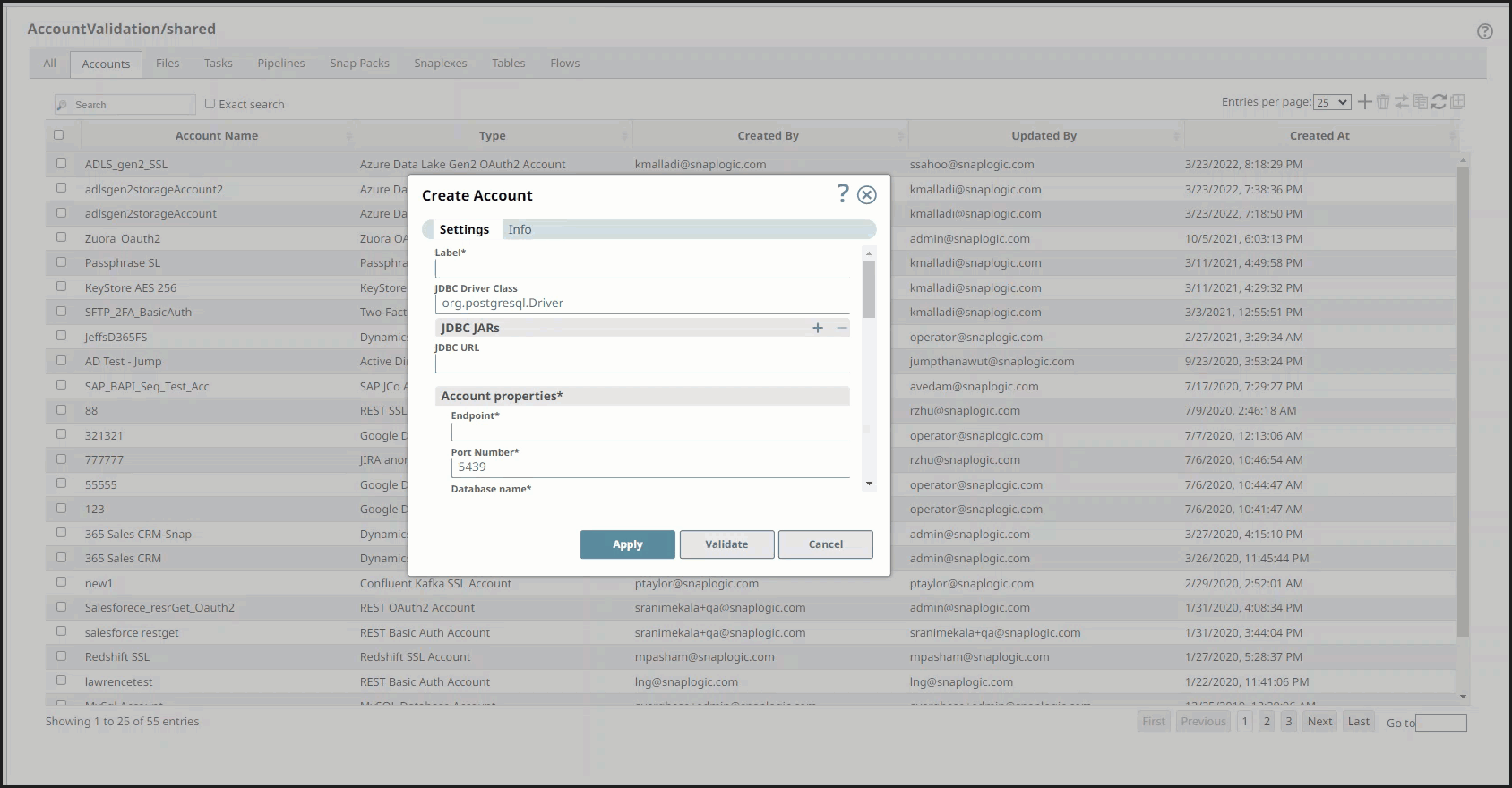
Enter the required account details. For detailed guidance on how to provide information required for each account type, see the following articles:
Click Validate to verify the account, if the account type supports validation.
Click Apply to complete configuring the Redshift account.
Enter additional information about this account in the Notes field of the Info tab. This will help you – and other users – understand the purpose of the account, especially if there are multiple accounts of the same type.
Configuring Redshift Accounts Using SnapLogic Manager
You can use Manager to create accounts without associating them immediately with Pipelines.
Accounts in SnapLogic are associated with projects. You can use accounts created in other projects only if you have at least Read access to them.
In the left pane, browse to the project in which you want to create the account and click > Account > <Snap Pack Name>, followed by the appropriate account type. The Create Account dialog associated with the selected account type is displayed.
Repeat the steps numbered 3 through 5 in the Creating an account section.
Supply the necessary information.
- URL parameters to be specified to ensure SSL connectivity:
ssl=true
- The S3 Bucket, S3 Access-key ID and S3 Secret key properties are required for Redshift-Bulk Load and Redshift-Bulk Upsert Snaps. The S3 Folder property may be used for the staging file. If the S3 Folder property is left blank, the staging file will be stored in the bucket.
- URL parameters to be specified to ensure SSL connectivity:
- (Optional) Supply additional information on this account in the Notes field of the Info tab.
- Click Apply.
Avoid updating account credentials while Pipelines using that account are executing. Doing so may lead to unexpected results, including your account getting locked.
- If the Snap fails to connect to the database, it will retry three more times.
- While selecting an Account on a Redshift SSL instance, you can use the JDBC driver v1.2.8.1005 or greater to validate it. However, when not using the Amazon's Redshift JDBC driver v1.2.8.1005 or greater, you would be required to manually import an updated certificate into their TrustStore or, simply use the Redshift SSL Account.
Have feedback? Email documentation@snaplogic.com | Ask a question in the SnapLogic Community
© 2017-2025 SnapLogic, Inc.